Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
Clear Cached SSL Certificates
Let's Encrypt DST Root CA X3 and intermediary R3 certificates have expired a couple days ago. I have a Plex server that uses a certificate from Let's Encrypt but it is signed by ISRG instead of DST. When I visit the site with an iOS or tvOS device I get a certificate error. Using the TLS Inspector app on my iPhone I am able to see that my Plex certificate is valid but the R3 and DST CA is expired causing it to fail. If I visit the site on a iOS device that never visited it before it works and I can see the certificate is valid. If I factory reset a device that isn't working then, after reinstalling, it works. This all points me to my device is caching the old intermediary and root certificate and refusing to update.
My question is how do I clear cached certificates on an AppleTV or iPhone? So far I have tried clearing Safari's cache, resetting the network settings, removing and reinstalling the app, and restarting the device and none of these have worked. This is different than if I manually trusted a certificate or have a certificate installed via a profile.
More info on the expired certificates can be found here:
https://letsencrypt.org/docs/dst-root-ca-x3-expiration-september-2021/
Safari shows this when I view the certificate:
More Details shows this:
As you can see the Plex certificate is valid but it shows it as expired. I used TLS Inspector to see the certificate chain and it shows this:
If I visit the same site on a non Apple device it shows the correct certificate chain:
[Image Edited by Moderator to Remove Personal Information]
Posted on Oct 3, 2021 7:16 PM
Posted on Nov 16, 2021 12:59 AM
This is very annoying. Lost about one whole week digging through the internet. Visiting the same site on a Mac with Firefox works fine -> FF has it‘s own certificates management.
I think the problem lays in the shared Trust Store. There you can still find the expired certificate. And if a device used this once for a site, it tries to use it again.
Similar questions
- Cannot trust self signed certificate on iOS 15.2 Hello, I am trying to install and trust a self signed root CA certificate on my device to access services hosted on my internal network. Importing and installing the certificate went well. I however do not have the option available to fully trust the certificate. I have the exact same issue than this one : https://discussions.apple.com/thread/253175842 No answer has been provided to this post, other than to switch the toggle on, but this toggle is not displayed at all. Are there any specific requirements to meet for imported certificate to show in this list? I tested different key length (2048, 4096), validity (10 years, 1 year) and signing protocol (sha256, sha512), with no luck. Update from iOS 15.1 to 15.2 does not fix the issue either. I have not been able to find any help on the Internet so far, apart from this article that does not help in this case, the toggle not showing up at all : https://support.apple.com/en-us/HT204477. Thanks a lot for your help. 1289 1
- Internal Certificates not trusted by iOS after Sept 1st, 2020 with validity period greater than 398 days.. The following post indicates that iOS devices will not trust certificates after Sept 1, 2020 with a validity period greater than 398 days for Root CAs pre-installed devices. This article also indicates that user or administrator added root CAs will not be affected. About upcoming limits on trusted certificates - Apple Support We took this to understand that our internal certificates from our company would not be affected, however this is not true. We found a workaround by setting a browser setting to trust all certs, however, some apps like Power BI do not work with the workaround in place. Is there any confirmation Apple can give that this would also affect the trust of certs not issued by public Root CAs but our own internal Root CA? 1649 2
- Self-signed certificate chain not trusted in iOS when only TLS Server Certificate to the web server Hi All, We have the following x509 certificate chain for a web server running in a private networks. +- Root CA Certificate (Self-signed) +- Application Signing Intermediate Certificate (Self-Signed) +- TLS Intermediate CA Certificate (Self-Signed) +- TLS Server Certificate (Self-Signed, Note: TLS server certificate follows these requirements: Requirements for trusted certificates in iOS 13 and macOS 10.15 – Apple Support (AU)) The certificates were deployed to the test iPhone SE and iPad (Root and TLS Intermediate CA certificates) devices, and web server (TLS Server certificates). In both devices, Safari shown connection are not private. When tested the same in Windows and Android (Samsung Galaxy Tab), the connections were all secured. When TLS Intermediate CA and TLS server certificates are combined into one PEM file, the connection became secured in both the iPad and iPhone SE. Is this the proper way? Do we need to deploy a certificate chain from after the root to the TLS server certificate? We didn't faced this issue during our initial development, the only difference is we didn't use a TLS Intermediate CA Certificate (our TLS server certificate is directly signed by the root CA). Currently, we have no idea why when just the TLS server certificate is deployed to the web server the connection is not secured but when the a certificate chain (TLS Server + intermediate) is deployed the connection becomes secure. 1824 4
Loading page content
Page content loaded
Nov 16, 2021 12:59 AM in response to choeschen
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Where are digital certificates physically stored on a Mac OS X machine?
Can someone tell me and maybe link to literature which describes it, where are the digital certificates storage location on Mac OS X? I know I could access the certificates with the “Keychain” application. But where are the certificates stored on the disk? Under Linux they are for example under /etc/ssl/certs but under Mac OS X they are no certificates in this folder.
I read something about that the certificates are stored in a “Keychain File?” Is this right? If yes, could someone explain me the technical details on it.
If someone has detailed literature of this stuff, would be helpfull to link them here. thanks!
- certificate
- trusted-root-certificates
Where are the digital certificates storage location on Mac OS X
Apple's Mac OS X includes a built-in key and password manager, Keychain, which stores user passwords, user and server certificates, and keys.
Source Certificate and Key Management in Mac OS X (Link no longer available)
Where is the Keychain data stored?
The keychain data is stored in ~/Library/Keychains/, /Library/Keychains/, and /Network/Library/Keychains/. The first location is where my personal keychain is stored. To access their data, I need the Keychain Utility located in the Utilities folder in the Applications folder. I like using spotlight to access the Keychain Utility as it only takes a few keys to get there – click on the spotlight icon in the top right corner and type “keychain”. Spotlight is quick and will predict what you are looking for and get it on top of the search quickly, so you don’t even need to type the whole word. Once you open it, you have access to your Keychain. Understanding Local Keychain Files I will briefly explain the purpose of the most important files in these directories. /Users/${OS_USERNAME}/Library/Keychains/login.keychain-db – This keychain is created when your user account in Mac OS X is created and normally has its password synchronised with your login password. It is unlocked at login and locked a logout. This is where most of your passwords will end up in. Its password is changed when you change your login password or using the Keychain Access utility. /Users/${OS_USERNAME}/Library/Keychains/${HARDWARE_UUID}/ – UUID stands for Universally Unique Identifier and this value is unique to your device. In the Keychain Access app, it appears as “Local Items” and is where your iCloud keychain is stored, when the service is enabled. The iCloud keychain service allows passwords and other types of data from it to be synchronised with your other Apple devices like you iPad, iPhone or another Mac. The only requirements are that all these devices are using the same Apple ID account, and the OS supports the iCloud keychain service (Mac OS X 10.9 and above, iOS 7.0.3 and above). /Library/Keychains/System.keychain – The System keychain stores items that are accessed by the OS and shared between users, for example, to allow everyone on the Mac to be able to connect to a WiFi network. Only administrators can change its content. /Library/Keychains/FileVaultMaster.keychain – This file is created by the system when FileVault encryption service is enabled on your Mac. The OS manages its content. /System/Library/Keychains/ – This is another location that can store loads of keychain files. Its content is managed by the system and other applications. Most of them will not appear in the Keychain Access utility however, all users benefit from it.
Source Understanding the Mac OS X Keychain (Link updated) by Ivaylo Mihaylov
Further Reading
- Mac OS X - Working with the System Keychain
- Is there a difference to OS X Server in the certificate store locations or management? On Windows Server there are much more stores etc. – Opa114 Oct 30, 2015 at 16:55
- 1 @Opa114 Sorry, I've no idea. Might be a good question for serverfault.com – DavidPostill ♦ Oct 30, 2015 at 16:58
- thanks for the hint. I aks there if i need more information. Do you have knowledge how the certificate Management on Unix / Linux are? – Opa114 Oct 30, 2015 at 23:18
- @Opa114 Not really. – DavidPostill ♦ Oct 30, 2015 at 23:28
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged macos mac certificate trusted-root-certificates ..
- The Overflow Blog
- Developers with AI assistants need to follow the pair programming model
- How do mixture-of-experts layers affect transformer models?
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
- Google Cloud will be Sponsoring Super User SE
Hot Network Questions
- Alternative control flows to highlight happy-path
- How are the sounds from the Sorting Hat produced?
- Is it dangerous to leave “.DS_Store” files left in Git commit history?
- Is multiplication of two complex numbers that are inside a complex regular polygon still in this polygon?
- LARP weapons - plastidip wrinkles
- init.lua - Remove default mapping recursively
- Does it matters who your thesis examiner is?
- Who is the black-haired character with a white and black / dark blue costume appearing in the parody of "A Different World"?
- Do languages have any sort of upper limit for how long it takes to say things?
- Will it be possible to prevent cancer by introducing ECC on genome?
- How might a Christian persuade a naturalist non-theist that the universe cannot be a brute fact?
- Dual Criminality for weapons?
- Please identify this program for Acorn Archimedes
- How to replace a file path with whitespace using sed?
- Proving Poincaré's inequality for Boolean functions over the hypercube without Fourier analysis
- Confusing use of "if" in "Advanced Grammar in Use"
- An Arena/Bump Allocator in C
- Serious device for making hummus at home
- How to Relate the Functional Derivative to Infinitesimal Change in Noether's Theorem
- Where can I find hardware details for the Philips VG-5000?
- Characteristic impedance of a BNC jack to jack adapter
- Staying out of the blind spot of a truck that doesn't have mirrors?
- What happens to an ongoing electrolysis when you turn off the battery?
- Non sequitur claims when deducing meaning from historical artifacts or texts (problem of presentism)

How to Check Digital Certificates on Computer and iPhone
There are two simple ways to ensure that things are safe quickly, and the website uses encryption with a certificate. First is the presence of a closed padlock icon in the URL bar, and the second is the beginning of the URL as HTTPS instead of HTTP.
Keep data safe. It is vital to ensure that the site you visit transmits your data securely or not. When you view a website’s Certificate, you come to know about the ownership and whether it is secure to transfer your data through this site or not. So if you are looking to view a website’s Certificate, here are easy steps to do so on Safari, Chrome, Firefox, Opera, and even iPhone.
What Details are in a Digital Certificate?
- Who issued the certificate? It may be VeriSign, DigiCert, GlobalSign, or Thawte. These are the companies that, after due process, determined the validity, trustworthiness, and related credibility of the website.
- To whom the certificate is issued? It is the website owner or organization to whom the certificate belongs. Ensure it matches the name of the website or the parent company or the name you expect when you visit that site.
The expiration date of the Certificate: This is mostly one to two years, but sometimes it can be longer than this.
How to View Digital Certificate in Safari
- How to Check Digital Certificates in Chrome
- How to See Certificate in Firefox
- How to Check Certificate in Opera
- How to View Digital Certificates on iPhone
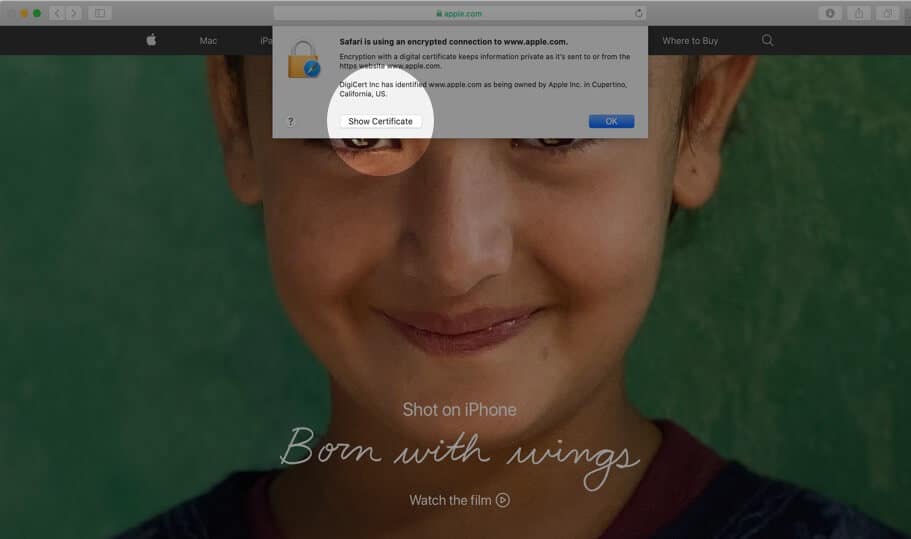
Step #1. Inside Safari on Mac, open the website whose certificate you wish to see.
Step #2. In the address bar, click on the padlock icon that is at the start of the URL.
Step #3. Click on Show Certificate from the small pop-up.
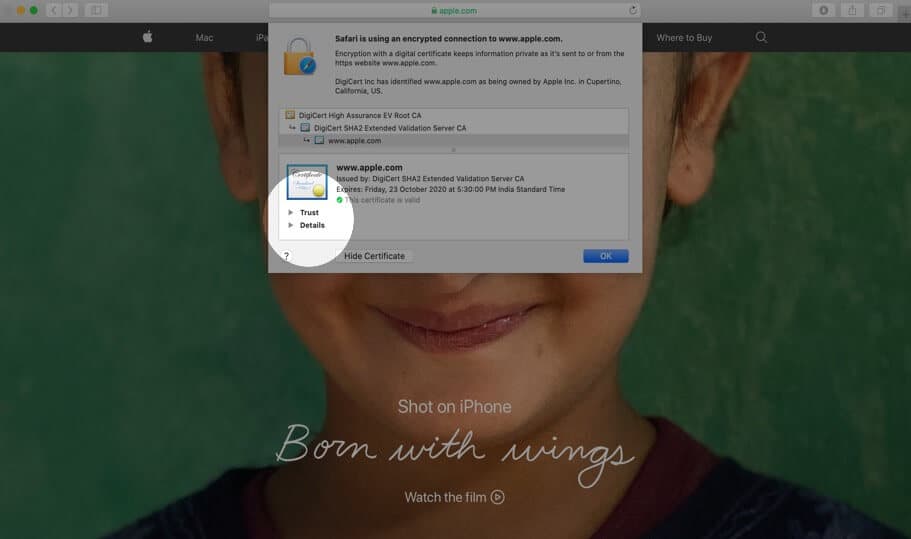
Step #4. Here you will see the certificate information as a summary. You may click on Trust and Details to expand and view the complete certificate.
How to View Digital Certificate in Chrome
Step #1. Open the website in Chrome.
Step #2. Click on the small padlock from the left of the URL.
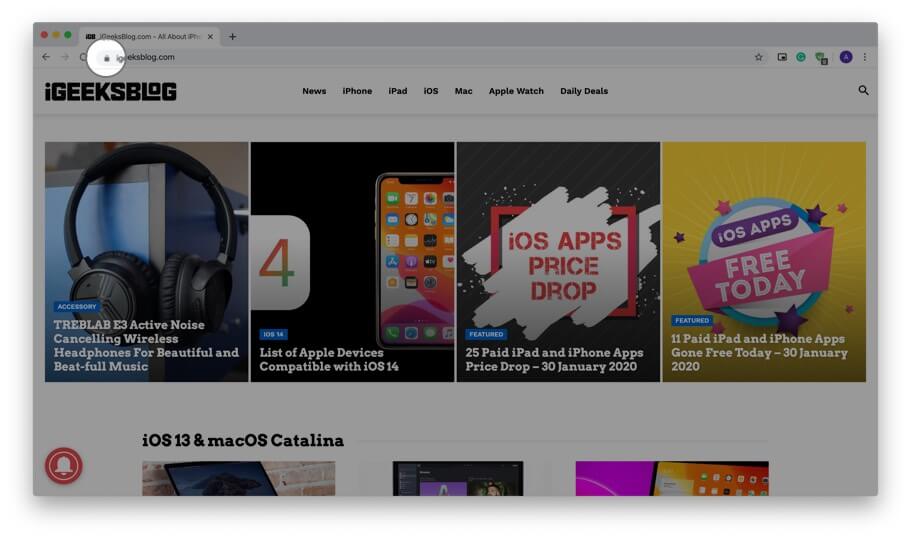
Step #3. Click on Certificate (Valid) from the small dropdown pop-up.
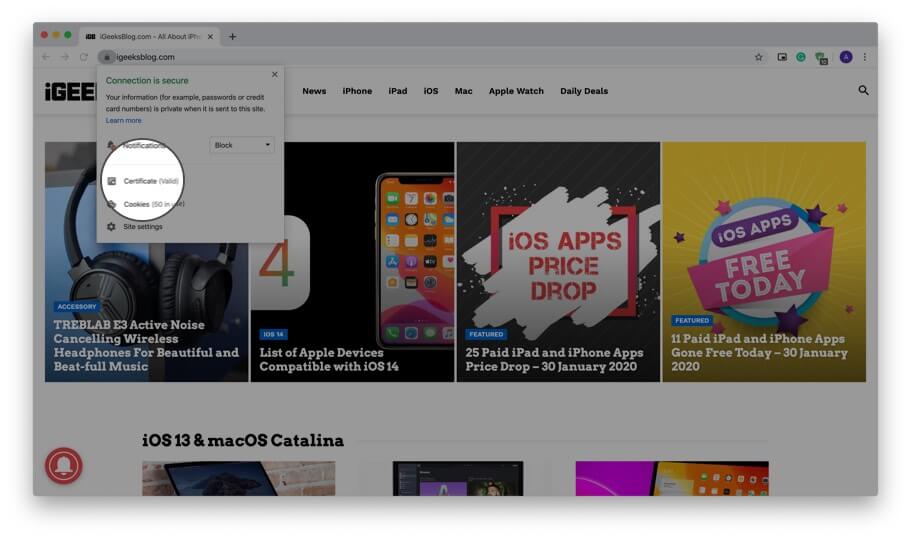
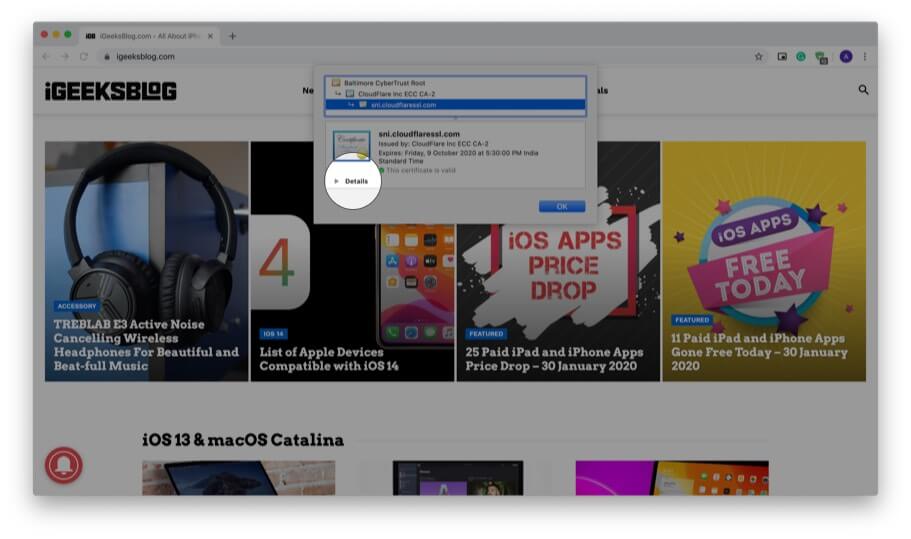
Step #4. Here you have a summary of the certificate information. Click on Details to view the entire certificate. You may scroll down to see everything.
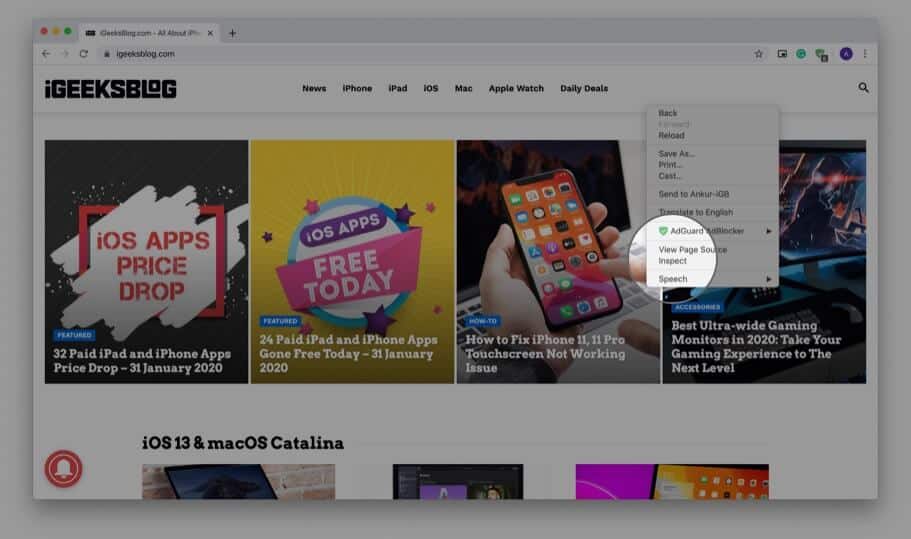
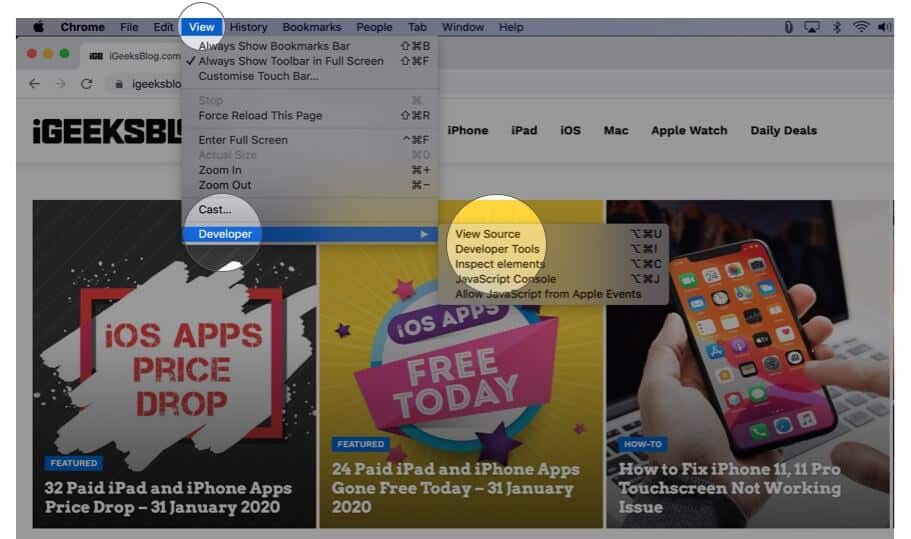
Use Developer Tools to View Digital Certificate in Chrome
In addition to the above method, you can also use developer tools menu to view the certificate.
Step #1. Place your mouse pointer, preferably on an empty place on the website and right-click. Now, Click on Inspect.
Step #2. Click on Security.
Note: If you do not see the Security tab, place your mouse pointer on the boundary of this pop-up and drag it to the left to increase the size. You may also click on the small double arrow and then click ‘ Security. ‘
Step #3. Click on View certificate.
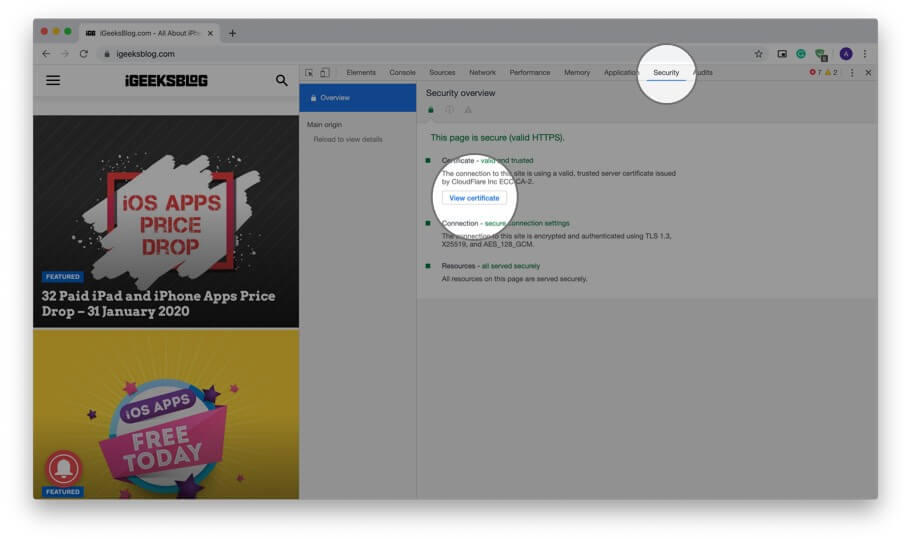
Note: If you are running Chrome on Mac, in Step #1, you may click on View from top menu bar → Developer → Developer Tools → Security → View certificate.
How to View Digital Certificate in Firefox
Firefox also lets you quickly view the certificate of the site you are visiting.
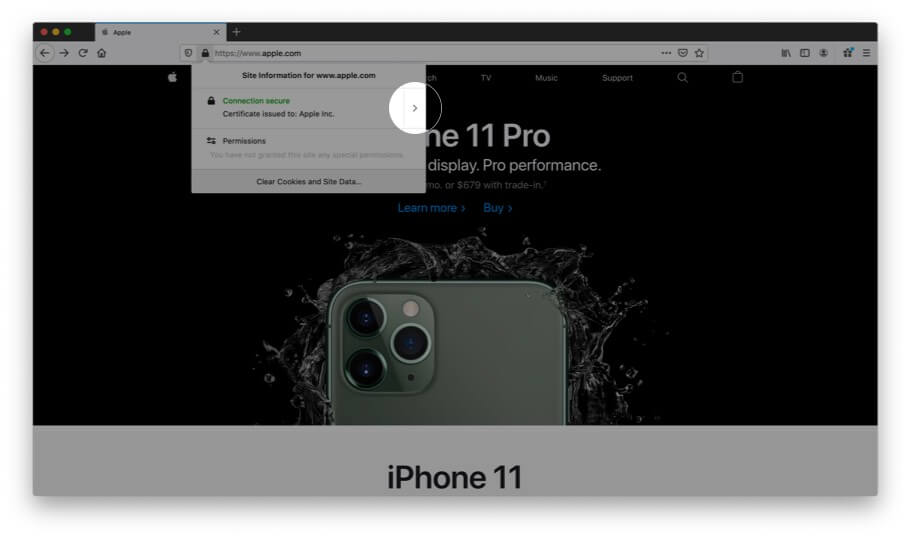
Step #1. Ensure you have opened the website in Firefox.
Step #2. Click on the padlock .
Step #3. Next, click on the arrow next to the words ‘Connection secure.’
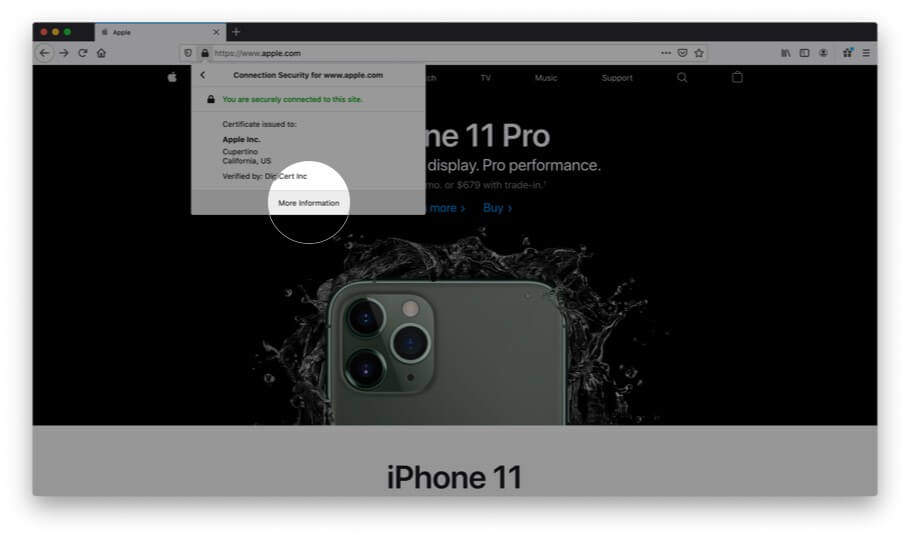
Step #4. Here you will see a few details. Click on More Information.
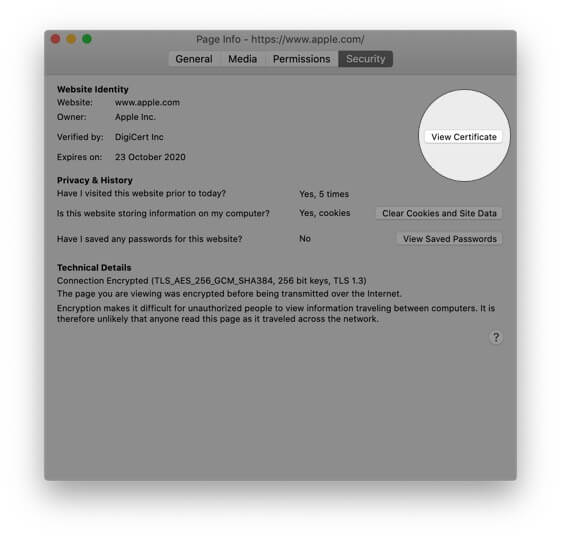
Step #5. A separate window opens that has many details. Click on View Certificate. It will open in a new tab with the website’s certificate details.
View All Certificates Inside Firefox
Step #1. Inside Firefox, click on three horizontal lines icon from the top right.
Step #2. Click on Preferences. It will open in a new tab.
Step #3. Now click Privacy & Security.
Step #4. Scroll down and under Certificates, click on View Certificates…
Step #5. Now from this pop-up double click on any certificate to open all its details.
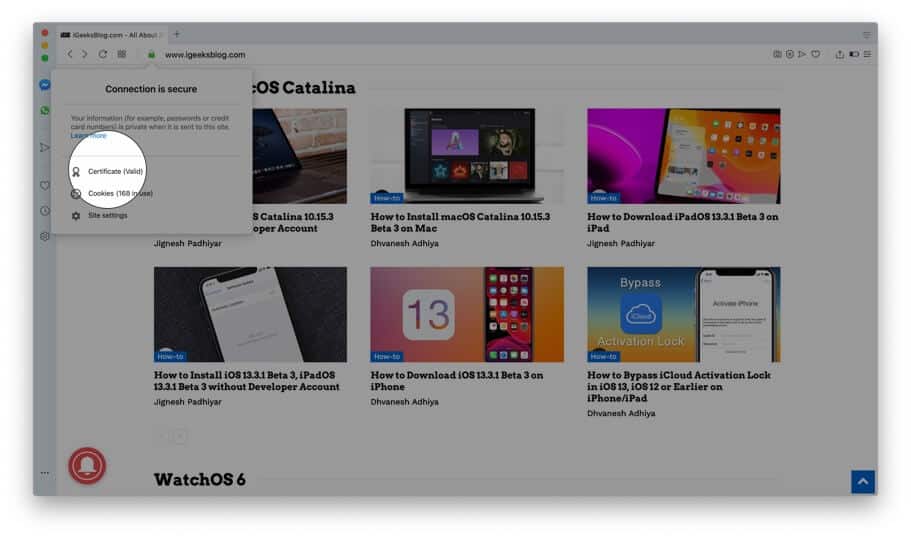
How to View Digital Certificate in Opera
Finally, let us see how to view certificates in Opera browser
Step #1. Open the website inside Opera browser.
Step #2. Click on the green padlock from the right of the URL.
Step #3. Click on Certificate (Valid) .
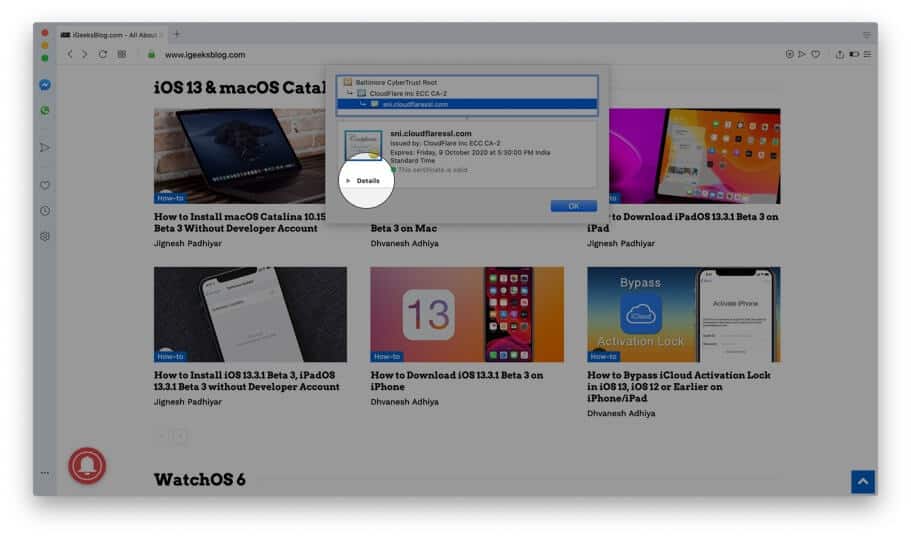
Step #4. Here, if you are looking for more info, you may click on Details.
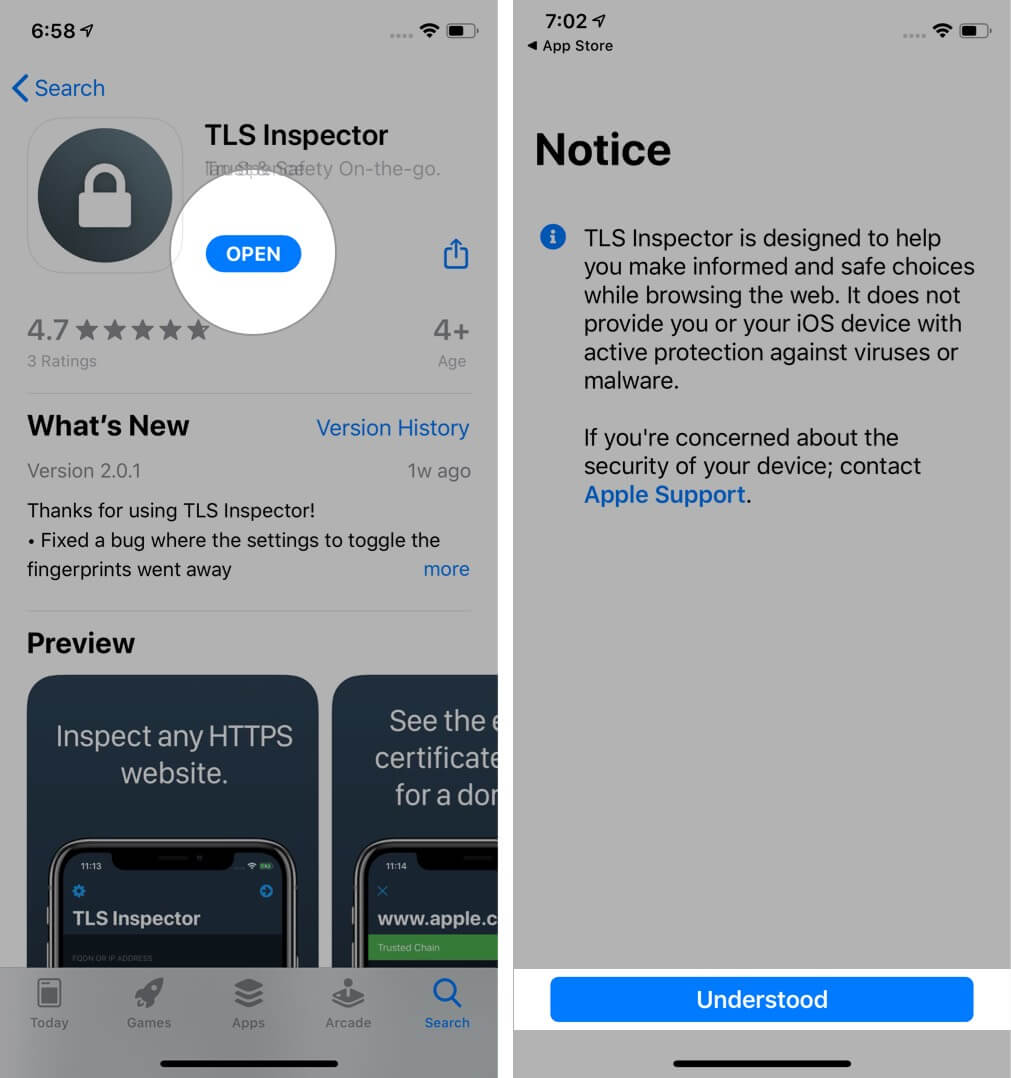
How to View Certificate on iPhone
It was easy and straightforward to see certificates on the computer version of Safari, Chrome, and other browsers. But, doing so on the iPhone is a bit complex. When you tap on the padlock icon in Safari (or Chrome) on your iPhone, it opens up the keyboard instead of showing the certificate. But we have a solution.
Step #1. Open App Store and download TLS Inspector .
Step #2. Launch this app and tap Understood.
Step #3. Here you can input the website address and quickly view the certificates.
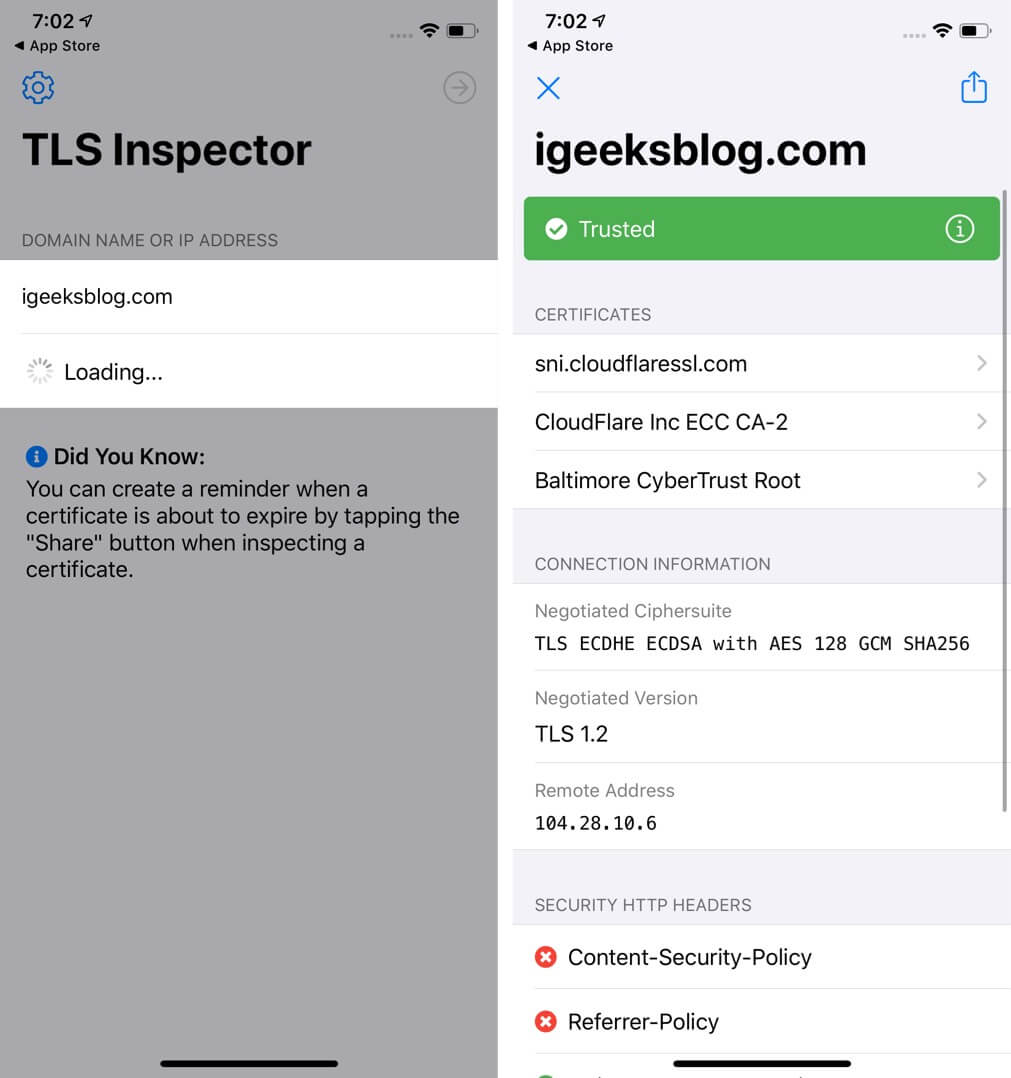
Alternatively, you can also use TLS Inspector extension inside Chrome or Safari to see the certificate there. You do not need to open this app. Read on.
How to See Certificate on iPhone in Safari
Step #1. Follow Step #1 and Step #2 above.
Step #2. Launch Safari and open the website.
Step #3. Tap on the share icon.

Step #4. Tap Show Certificate or Certificate.
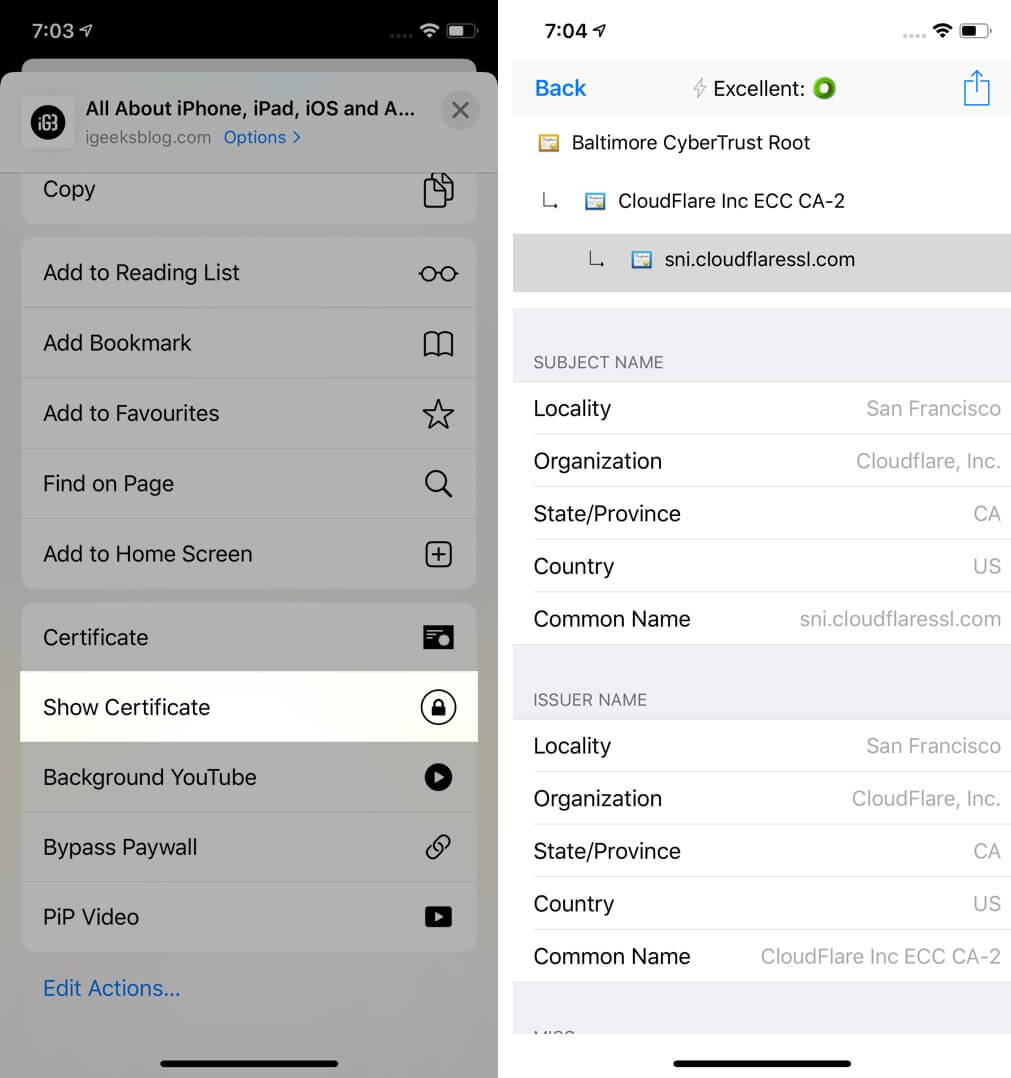
There you go!
How to Check Certificate on iPhone in Chrome
In Chrome, you can see a concise summary without needing any other app. You can see whether the connection is secure or not by following the steps below.
Step #1. Open the website in Chrome on your iPhone.
Step #2. Tap three dots icon → Site Information. In a small pop-up you can see the relevant information in brief.
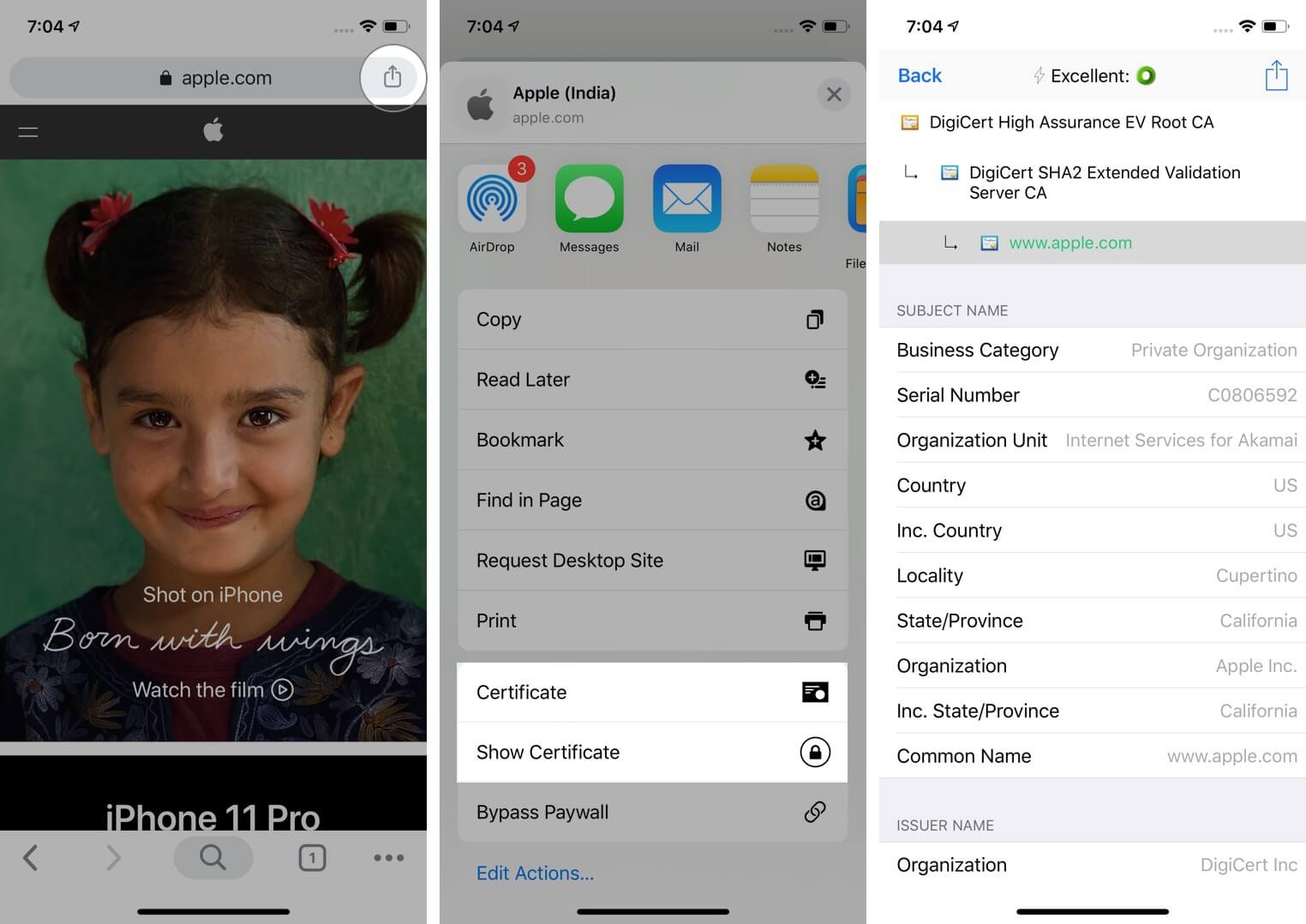
To view the full certificate in Chrome, follow Step #1 and Step #2 under ‘How to view Certificates on iPhone.’ Next, tap on the share icon that is in the Chrome URL bar. Finally, tap Show Certificate or Certificate.
Signing off…
This is how you can view certificates inside various browsers. I also showed you how to do so on an iOS device. I hope this post was helpful to you. Kindly share what you feel in the comments down below. If you have additional ways, let us know that too.
You may like to read…
- Best Security Apps to Keep Your iPhone and iPad Secure
- Top 5 Apple Watch Security Features: Double Down on Privacy
- How to disable ‘Trust This Computer’ alert on iPhone and iPad
🗣️ Readers like you help support iGeeksBlog. When you make a purchase using links on our site, we may earn an affiliate commission. Read Disclaimer .
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
How to generate a new Safari Website Push Certificate
Action Needed: Website Push Certificate Expires in 30 Days. Your Website Push Certificate will no longer be valid in 30 days. To generate a new certificate, sign in and visit Certificates, Identifiers & Profiles .
If you run a website that send browser push notifications, you have most likely received this email from Apple reminding you that your push certificate for Safari is about to expire. I’ve been receiving the same email for several years now, but every time I scratch my head wondering how do I do that again.
So this year, I decided to write down the steps and publish them for everyone (but mostly me) to follow again in the future when it’s time to renew the Safari push certificate.
How to renew a Safari Website Push Certificate
In order to generate a new Safari Website Push Certificate, you will need a paid developer account. First you will have to request a certificate from a certificate authority using Keychain Access on your Mac, then you will need to create a Web Push Certificate. We’ll walk you through each step with simple instructions and illustrations.
Note that the following instructions are to generate a Safari push certificate for a website that is already registered to send push notifications. If your website is not registered yet, make sure to login to your Developer account, click on Identifiers and then click on Register an App ID. Then select Website Push IDs and click Continue. Type in a description, an identifier, and then click Continue to finalize the registration. Once done, you may go on with the instructions below.
1) First we need to make a certificate signing request. Open Keychain Access on your Mac, then navigate to Keychain Access > Certificate Assistant > Request a Certificate From a Certificate Authority…
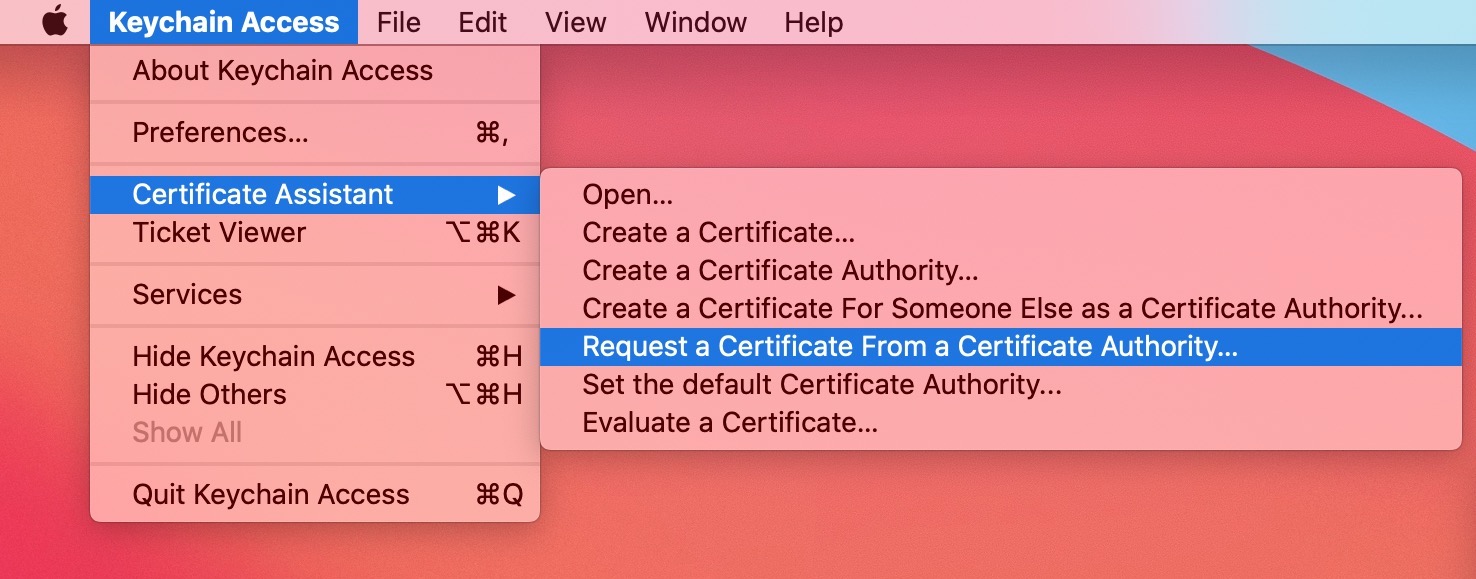
2) Enter your email address and your name, which should already be pre-filled. Leave the CA Email Address field blank, and select to save the request to the disk .
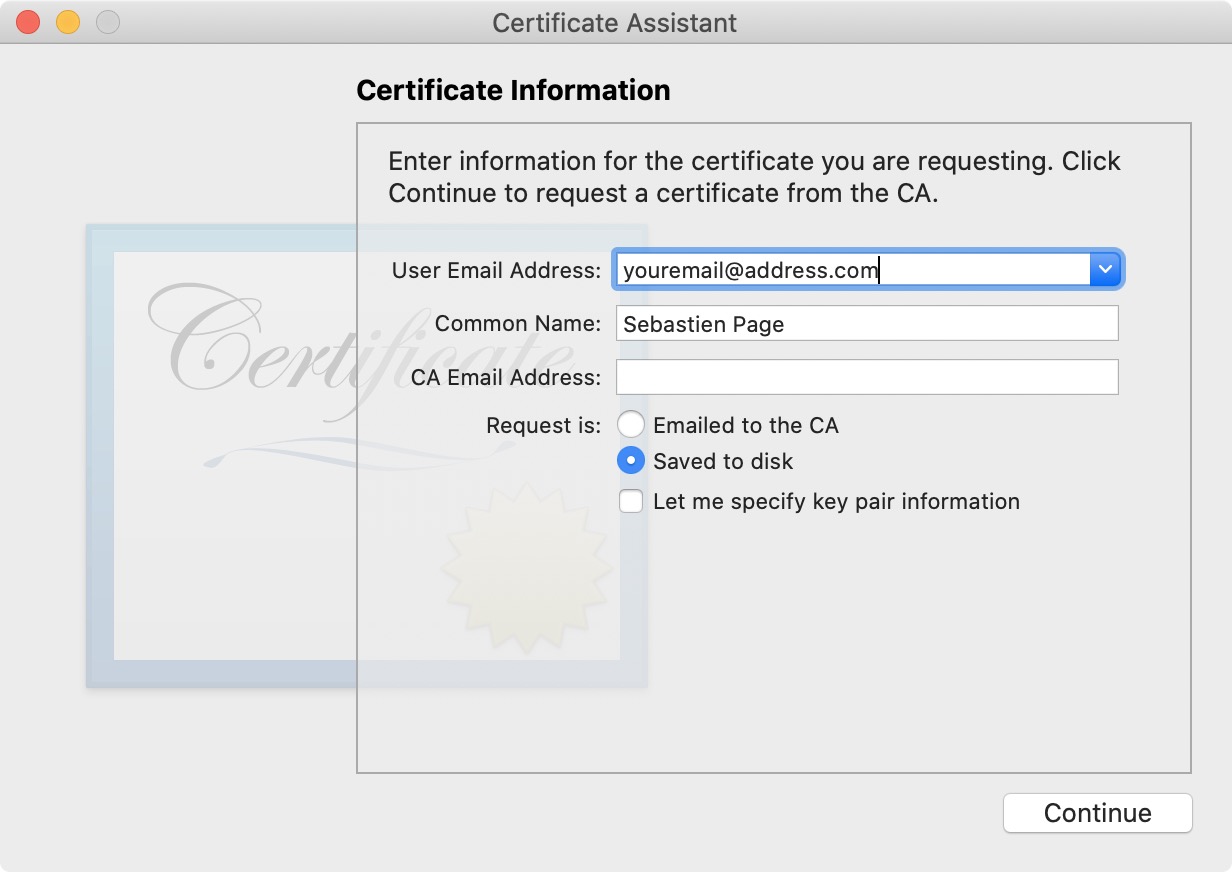
Click Continue, and make sure you save the file to your Desktop for easy reference. You should now have a file titled CertificateSigningRequest.certSigningRequest on your Desktop.
3) Sign into your developer account at developer.apple.com, then click on Certificates, Identifiers & Profiles in the sidebar, and then click on Identifiers in the sidebar.
4) Click on the dropdown menu at the top right corner of the screen and select Website Push IDs .
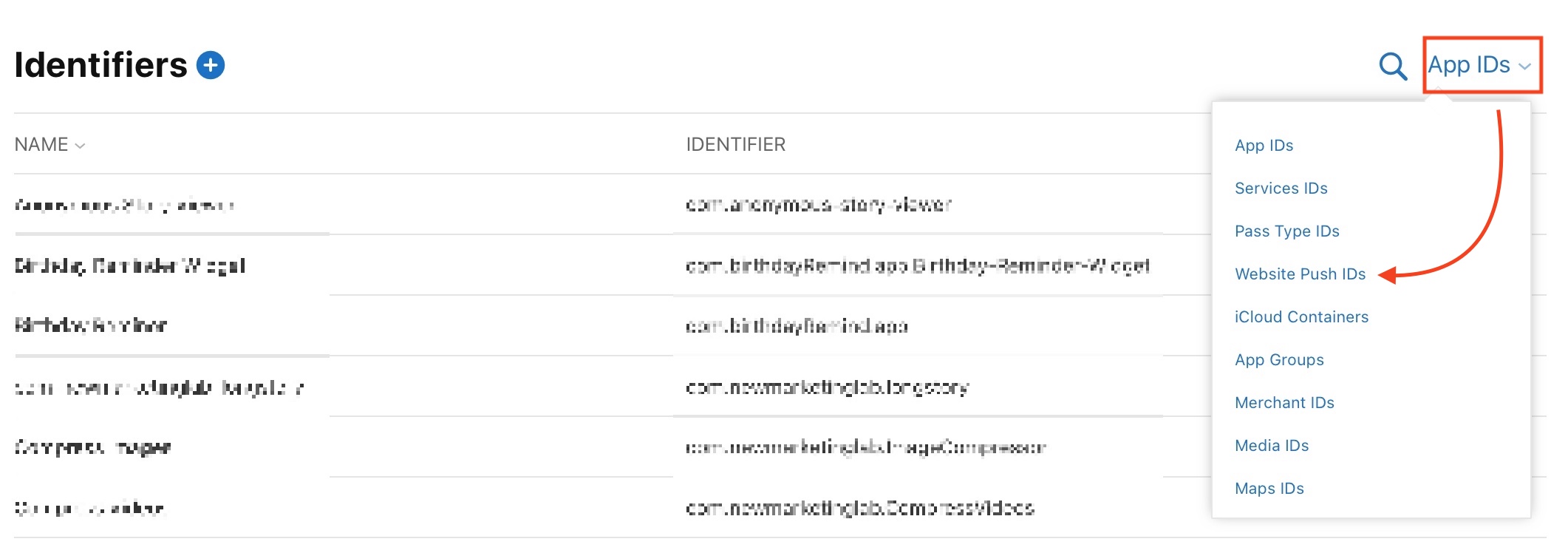
5) Click on the website push ID to select it. Unless you run multiple websites, there should only be one option in there.
6) Now we need to upload the CertificateSigningRequest.certSigningRequest file we saved to the Desktop in step 2. Click on Create Certificate , and then click on Choose File . Navigate to your Desktop, and select the CertificateSigningRequest.certSigningRequest file. Click Continue.
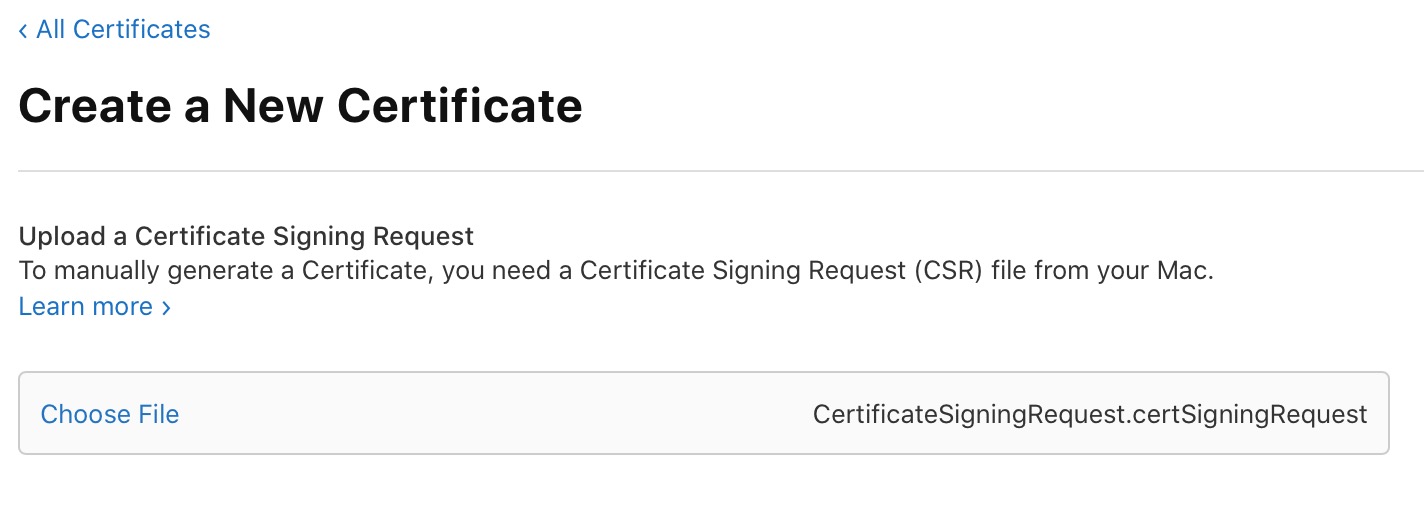
7) Finally, click the Download button to download your certificate, and save it to your Desktop. It will save a file named website_aps_production.cer to your Desktop.
8) Double click on the website_aps_production.cer file to open it in Keychain Access. If prompted, make sure to select login in dropdown menu, as seen below.
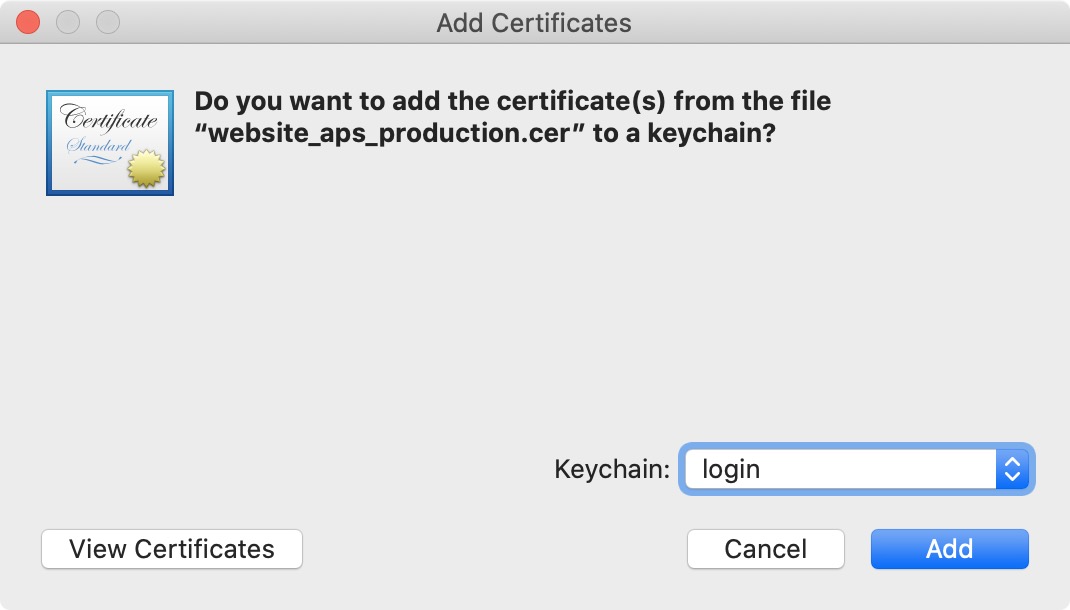
9) In Keychain Access, select the Certificates tab from the sidebar, and locate the certificate we just added. It’s pretty easy to tell which one it is because its expiration date should be exactly one year from today. Right click on the file and select Export Website Push ID .
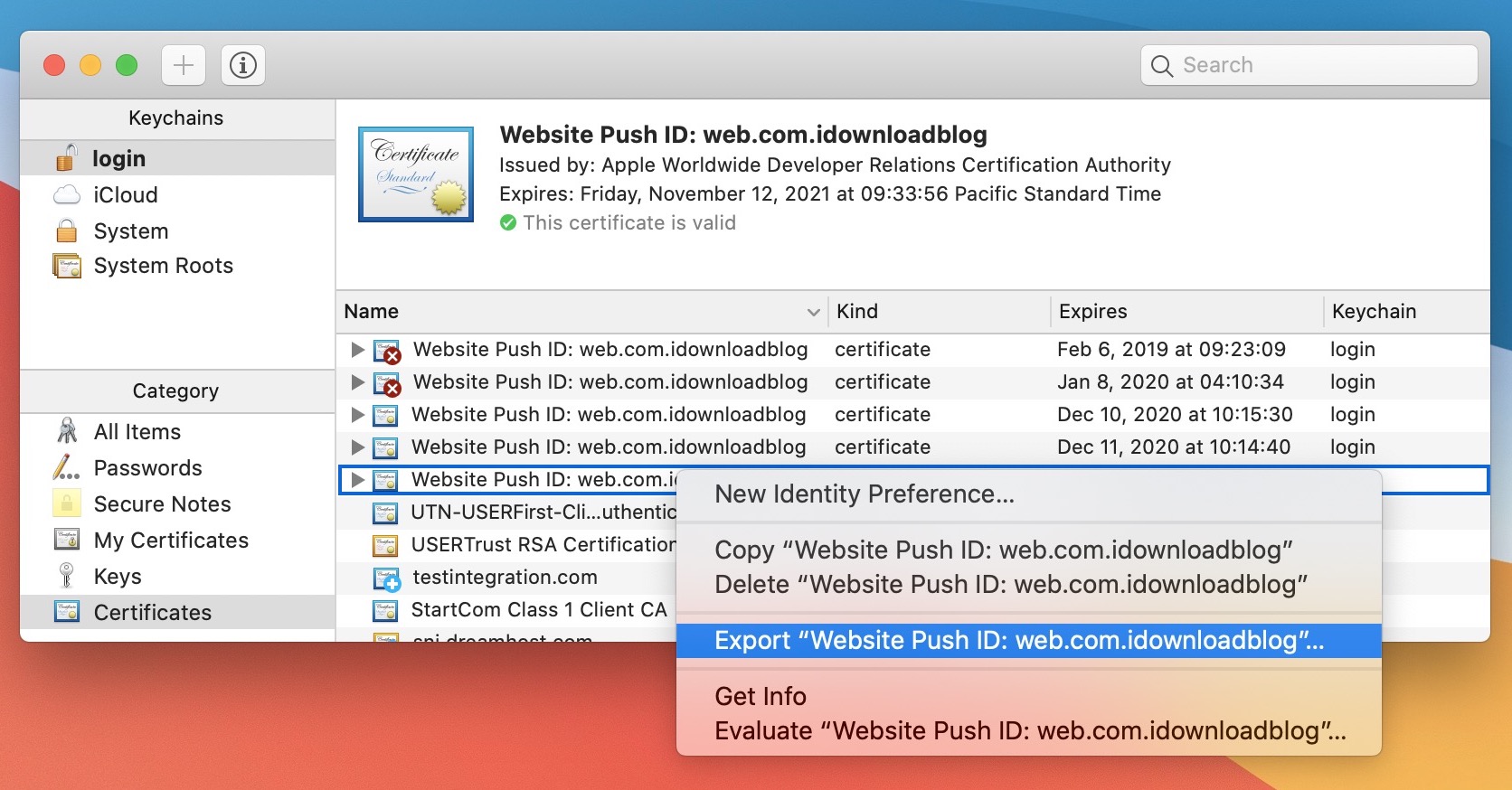
10) When prompted, make sure to save the Certificates.p12 file to your Desktop. If prompted to password-protect the p12 file, do not enter any password. Just click OK. You will however have to enter your admin password to export and save the p12 file.
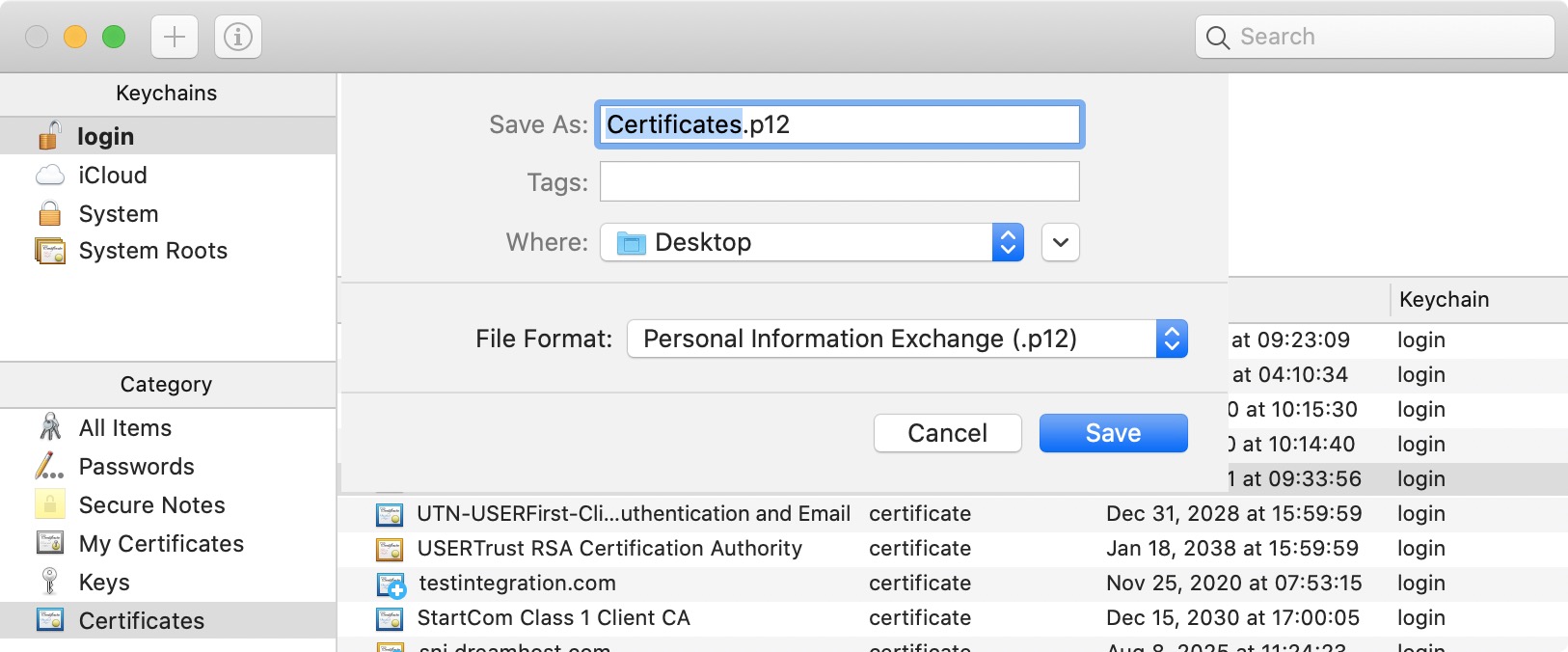
With the p12 file now on your Desktop, you may upload it to your push notification service of choice, such as OneSignal, WebPushr, etc.
Related: How to renew your Apple Developer Distribution Certificate
Apple Root Certificates
Apple established the Apple Root Certification Authority and the Apple PKI in support of the generation, issuance, distribution, revocation, administration and management of public/private cryptographic keys that are contained in CA-signed X.509 Certificates.
System Root Certificates
To better protect Apple customers from security issues related to the use of public key infrastructure certificates and enhance the experience for users, Apple products use a common store for root certificates. You may apply to have your root certificate included in Apple products via the Apple Root Certificate Program.
For iTunes related questions, please refer to the iTunes support page.
Assistance with "how-to" questions such as security configuration, clarification on security notices, or requests for software updates fall under the standard fee-based technical assistance program.
Software Update
Questions about Software Updates and Security Updates are best addressed via Apple's Support website.
DigiCert High Assurance EV Root CA Intermediate Certificate
When decryption is enabled on the Palo Alto Networks firewall, the end user might be presented with a forward untrust certificate from the Palo Alto Networks firewall. Normally, we'd expect to see the forward trust certificate for DigiCert High Assurance EV Root CA intermediate certificate used on the end server that is being accessed by the user.
Use the links Test tool 1 and Test tool 2 to know if the intermediate DigiCert High Assurance EV Root CA is supported by your browser. The Palo Alto Networks firewall should the forward trust certificate to the end user for these test tools.
Security Certificate Errors
DigiCert SSL certificates expiring after January 2011 are issued from a 2048 bit certificate path. The Root Certificate in this path is titled "DigiCert High Assurance EV Root CA" and is already trusted by all modern browsers (Internet Explorer, Firefox, Safari, Opera, Chrome, etc.)
To maintain widespread compatibility with older browsers and some mobile devices, DigiCert provides a Cross-Signed Intermediate Certificate which enables legacy devices to follow the intermediate certificate chain to the "Entrust.net Secure Server Certification Authority" Root Certificate. This Cross-Signed certificate appears in your Intermediate Certification Authorities certificates store in Windows. Its Subject is "DigiCert High Assurance EV Root CA" and its Issuer is "Entrust.net Secure Server Certification Authority."
- Update the end user's browser.
- Check if there is any difference between the intermediate DigiCert High Assurance EV Root CA presented by the server/website and the same certificate present in the Device > Certificate Management > Certificates > Default Trusted Certificate Authorities
Other users also viewed:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CleYCAS&refURL=http%3A%2F%2Fknowledgebase.paloaltonetworks.com%2FKCSArticleDetail
- 3.8 • 1万件の評価
Webを超高速で閲覧でき、強力なプライバシー保護機能と強力なカスタマイズオプションを備えています。Safariでは、サイトをブラウズしたり、Webページを翻訳したり、開いているタブにiOS、iPadOS、macOSのすべてでアクセスしたりできます。 機能 • iPhone、iPad、Macの間でパスワード、ブックマーク、履歴、タブなどをシームレスに同期できます • プライベートブラウズモードでは履歴が保存されないため、閲覧しているものは自分にしか見えません • インテリジェントトラッキング防止機能により、閲覧したWebサイト間でのトラッカーによる追跡が阻止されます • タブグループを使うと、複数のタブを保存および整理して、iOS、iPadOS、macOSのすべてでアクセスできます • プロファイルを使って、ブラウズ履歴やWebサイトデータなどを仕事用や個人用などのテーマごとに分けることができます • 共有タブグループは、家族や友達とタブを共有して共同作業を行うのに役立ちます • 機能拡張を使ってSafariをパーソナライズできます。ブラウザにさらに機能を追加することもできます • リーダーでは、広告、ナビゲーションやその他の気が散るものを取り除いて読みやすくしたフォーマットで記事が表示されます • プライバシーレポートには、自分を追跡することが阻止された既知のトラッカーが表示されます • リーディングリストを使うと、簡単に記事を保存してあとで読むことができます • 音声検索では、音声だけでWeb検索を行うことができます • Webページの翻訳では、Webページ全体をブラウザ内で直接ほかの言語に変換することができます • Handoffを使うと、Safariでしていることをデバイス間で簡単に引き継ぐことができます • “ホーム画面に追加”で、WebサイトやWebアプリをホーム画面から素早く開くことができます
ツリー表示と大きなスクショは旧世代の代物
iPad版のSafariのレビューです。PCとAndroidも使っている私から見て、iPadのSafariは『お気に入り』の表示の仕方が他のあらゆるブラウザ、ブックマークサービスから頭3つ差くらい抜き出ています。アプリを立ち上げた直後に48個ものブックマークとフォルダがたった1画面に見易く収まっています。「アイコンと少なめのテキストで並べる」このシンプルな構図が最も見易いです。私はブックマークを1100以上登録していますが、短いテキストでも瞬時に理解出来る様に、登録する際ショッピングサイト等のページタイトルの頭に付いている「Amazon」とか「楽天市場」とかをわざわざ省いて登録しています。そうまでしてでもブラウジングはSafariでやった方が良く、1100のブックマーク数が少なく感じる程の視認性の高さです。無意味なブックマークにタイトルを付けて区切り線の代わりにし、なるべく階層は増やさない様にもしています。現状ブラウザはツリー表示か大き過ぎるスクリーンショットのどちらかしか無く、その間を柔軟に埋められるブラウザが存在していません。ギャラリーアプリには、タイル数を柔軟に変えられる物が多いのに、ブラウザのブックマークはずっと旧世代でした。そういった現状でSafariが抜き出ているのは当然の結果だと思います。難点は他のOSでの制作を止めた事、iCloudブックマークも息をしていない事です。iPadなら持ち歩ける上に最高のブラウジングが可能になるので、スマホはAndroidですがタブレットは私の中だとiOS一択になっています。しかし、他OSとの同期が弱過ぎる点はどうしても無視出来ず、将来的には使用を止めなければならないブラウザの筆頭でもあります。残念ながらこれに依存するのはリスキーです。
フォームへの自動入力の挙動がおかしい
ある予約サイトなどのフォーム入力で、ID、ニックネーム、名前、ふりがな、電話番号、メールアドレスなどを入力する際に設定済みの連絡先けら自動入力を使って入力する際に、「連絡先を自動入力」で一括入力すると思い通りのフォーム入力にならないので、「連絡先を自動入力」の下に表示される入力候補文字列から1項目づつ選択して入力していましたが、IOS 15.4 以降の挙動がおかしくなって使いにくくなりました。 第一入力項目をタップし、先ず候補から文字を選択すると、文字は正常に入力され、次の第2項目へ自動でフォーカスされるのですが、その際、本来表示される筈の文字列候補が表示されないのです。第3, 第4項目でも同様です。 自動でフォーカスされるとそのような現象になる様で、一旦フォーカスを手動で他の項目へ移すなどして再度手動でその項目にフォーカスを当てると、本来の正しい文字候補は表示されます。 どうやら safari 連絡先 自動入力のバグと思われます。 早急な改修をお願いいたします。
また人のレビュー消された
Safari以前に、このAppStoreの不具合もなんとかしろ。レビュー記入中に別アプリに切り替えて戻ってきたら、編集内容が消えるどころか元のページすら残らずに最初のApp検索のところに戻されてる。最後にも言ってるが、ユーザーの都合を考えろ。 JavaScriptの設定変更が即時反映されない件をかなり以前から不具合報告のページに投稿してにもかかわらず、それを含めて諸々の不具合や不都合な仕様その他が全く何も直ってないという旨を自分の元のレビューに追記したら抹消してきよった。 ほんまここの会社、終わりやな。ユーザーの意見に耳を貸さず勝手なことばっかりやってな。OS15からほんまにあらゆるところがひどい。開発部門の人件費削減で中学生でも雇ってるのかと思う。要らないことばかりしてきとる。ピンチインでタブ一覧になるのも迷惑な時があるし、お気に入りの並べ替えでドラッグした時にイビツな動きをして以前と違って全くスムーズじゃなくなった。なんであんなにおかしい動きをするのか。プログラミングで根本的に間違ったことをしてるとしか思えない。それにお気に入りは、編集モードがあるのに通常時に長押しドラッグで移動になる必要が全くない。ポイントサイトなどでログボのためにアクセスだけしてプレビュー見る必要もない時もあるのに、下スワイプのタイミングが早いとブックマークの場所が変わってしまって、すぐに元の位置に戻しておかないと次の時に探さないといけなくなることもある。 いろいろなことがユーザーの都合無視で不便なものになっていってばかりしてる。 〝人が使うもの〟ということを考えろ。お前らの勝手なくだらない仕様を押し付けてくるな。変更を加えてくればくるほど使いにくくなってる。
デベロッパである" Apple "は、アプリのプライバシー慣行に、以下のデータの取り扱いが含まれる可能性があることを示しました。詳しくは、 デベロッパプライバシーポリシー を参照してください。
ユーザに関連付けられたデータ
次のデータは収集され、ユーザの識別情報に関連付けられる場合があります:
ユーザに関連付けられないデータ
次のデータは収集される場合がありますが、ユーザの識別情報には関連付けられません:
プライバシー慣行は、ご利用の機能やお客様の年齢などに応じて異なる場合があります。 詳しい情報
日本語、 アラビア語、 イタリア語、 インドネシア語、 ウクライナ語、 オランダ語、 カタロニア語、 ギリシャ語、 クロアチア語、 スウェーデン語、 スペイン語、 スロバキア語、 タイ語、 チェコ語、 デンマーク語、 トルコ語、 ドイツ語、 ノルウェー語 (ブークモール)、 ハンガリー語、 ヒンディー語、 フィンランド語、 フランス語、 ヘブライ、 ベトナム語、 ポルトガル語、 ポーランド語、 マレー語、 ルーマニア語、 ロシア語、 簡体字中国語、 繁体字中国語、 英語、 韓国語
- デベロッパWebサイト
このデベロッパのその他のアプリ
Apple Books
Apple Podcasts
あんしんフィルター for docomo
ポルノシールド - サファリのアダルト&広告ブロックサイト
Dark Browser-ブラウザ
プライベートウェブブラウザ・シークレットモード
Firefox: Private, Safe Browser
Sidebar Sync for Arc Members
A safari experience like no other
Spend the Night

Welcome to Safari West
Go on safari.
Unleash Your Wildheart
Start the Adventure Group visits click here
Safari Glamping
Arrive as a Guest - Return as a Wild Friend
Dining in the Wild
Sonoma's South African Braai Experience
Private Adventures
Come face-to-face with the wildest animals around on your very own Private Safari Adventure!
Ibis, Northern Bald
This conservation success story was recently downlisted from Critically Endangered to Endangered. Hooray!
Read More Show another animal
Safari West Happenings
See all Happenings
Safari West Presents! Land Paths
Conservation Dinner Series: Craig Anderson, of the LandPaths , joins us in the elephant room after dinner to give a talk about the need to have kids connect to nature.
Explore Share
Safari West Presents! Zooarchaeologist Jun Sunseri
Conservation Dinner Series: Kojun "Jun" Ueno Sunseri, Ph.D., RPA joins us in the elephant room after dinner to give a talk about bones/skulls.
Inspiring Wildlife Posts
See all News
You OTTO know it's my birthday!
Otto was born to proud parents, Eesha and Ongava on April 2nd, 2023. Named in honor of Peter Lang's father,...
The Incredible Story of the Laysan Duck
People usually come to Safari West to see the showstoppers—giraffes, rhinos, cheetahs, or zebras. While these are all incredible animals,...
Think Your Family is Bananas? So is Ours
The Holidays are here and it’s no secret that getting your troop together can be as stressful as fun. But...

- Introduction
- Privacy Policy
- Release Information
- Release Engineering
- Porter's Handbook
- Developer's Handbook
- Manual Pages
- Presentations and Papers
- Documentation Project Primer
- All Books and Articles
- Mailing Lists
- User Groups
- FreeBSD Journal
- Q&A (external)
- Project Ideas
- Git Repository
- GitHub Mirror
- Code Review (Phabricator)
- Continuous Integration Service
- Security Information
- Bug Reports
- Submitting Bug Reports
- Monetary Donations
- Hardware Donations

- Search forums
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature currently requires accessing the site using the built-in Safari browser.
- Base System
Howto install a private CA certificate?
- Thread starter Henning Kessler
- Start date Aug 19, 2020
Henning Kessler
Karma: 2 Posts: 18
- Aug 19, 2020
Hello, is there somewhere a working howto that shows how to add a private CA (2 intermediate certs and one root cert) to FreeBSD 11.3? I found this one ( https://blog.socruel.nu/freebsd/how-to-install-private-CA-on-freebsd.html ) but I can't make it to work. Testing the CA file directly works: Code: openssl s_client -connect host:443 -CAfile ca.pem ... Verify return code: 0 (ok) Any help would be great Regards Henning
Karma: 1,288 Posts: 1,143
It depends on what you want to do with the certificate. This has very little to do with FreeBSD itself. For example, if you want to use it for a web server, you have to install it in your web server’s configuration. Consult your web server’s documentation for that. In the case of Apache httpd, you usually store them in /usr/local/etc/apache*/ssl , and you might have to make small changes to a configuration file. If you want to make the certificate known to your web browser, then it depends on the browser. For example, in Chrome open the settings page and go to the “Privacy and security” section, then select the “Manage certificates” entry. To make the certificate available to OpenSSL-based applications, put it in /etc/ssl/certs .
- Thread Starter
Hi olli, my intention was to make all OpenSSL-based applications trust the certificates which has been and will be signed by those CA certificates. I can verify the certificate chain by using openssl s_client -connect with the -CAfile option but when I put that file into /etc/ssl/certs and run the same command without the option the return code changes from 0 (ok) to 21 (21 (unable to verify the first certificate).
Karma: 34 Posts: 95
- Aug 20, 2020
Henning Kessler said: Hi olli, my intention was to make all OpenSSL-based applications trust the certificates which has been and will be signed by those CA certificates. Click to expand...
ondra_knezour
Karma: 272 Posts: 858
Henning Kessler said: [...]but when I put that file into /etc/ssl/certs and run the same command without the option the return code changes from 0 (ok) to 21 (21 (unable to verify the first certificate). Click to expand...
Hi there, thanks for all your help. Adding the certs to /usr/local/share/certs/ca-root-nss.crt did work, but re-adding them every time the package gets updated is not so great. Is there way to set -CApath option as default in a .conf file? And how can the ca-root-nss then be. added as well? Henning
mmh now this is strange or better embarrassing for me ;-). I deleted the CAs from the bundle file and created the hashs from the CA files with sudo openssl x509 -noout -hash -in CA.pem created the symbolic links ln -s CA.pem HASH-FROM-CMD-BEFORE.0 in /etc/ssl/certs and it works now.... So sorry stealing all your time Regards Henning
Karma: 176 Posts: 446
openssl rehash <folder containing certificates> should do the equivalent of the two commands above. Unfortunately, the man page for this gets tromped by the shell builtins rehash() one.
Just tried that command but in my 11.3 jail I get this response Code: openssl:Error: 'rehash' is an invalid command. it looks like the rehash option comes with 12.0
ljboiler said: openssl rehash <folder containing certificates> should do the equivalent of the two commands above. Unfortunately, the man page for this gets tromped by the shell builtins rehash() one. Click to expand...
Karma: 3 Posts: 1
- Oct 3, 2022
Found simple way: https://www.linuxpedia.pl/articles/freebsd-certs/ 1. Copy certificate to /usr/local/etc/ssl/certs (create if necessary). 2. Run certctl rehash - it will put it in all the places necessary and update respective databases/links.
- Jan 24, 2023
seregasoft said: Found simple way: https://www.linuxpedia.pl/articles/freebsd-certs/ 1. Copy certificate to /usr/local/etc/ssl/certs (create if necessary). 2. Run certctl rehash - it will put it in all the places necessary and update respective databases/links. Click to expand...
- Jan 26, 2023
I think both browsers have (or at least had some time ago) private certificate store where you can import own/custom certificates. Like here https://docs.titanhq.com/en/55958-importing-ssl-certificate-in-mozilla-firefox.html
- Jan 30, 2023
ondra_knezour said: I think both browsers have (or at least had some time ago) private certificate store where you can import own/custom certificates. Like here https://docs.titanhq.com/en/55958-importing-ssl-certificate-in-mozilla-firefox.html Click to expand...
Administrator
Karma: 18,061 Posts: 45,701
Firefox on Windows also ignores Window's certificate store and simply uses its own store.
SirDice said: Firefox on Windows also ignores Window's certificate store and simply uses its own store. Click to expand...
crt0r said: This behavior can easily be changed in the browser's settings. Click to expand...
SirDice said: Not allowed to change the browser's settings at $DAYJOB. And the desktop hosting team hasn't configured this. Which is funny, because I am allowed to add CA certificates to Firefox's store. So it's always a pain when they connect a new client and I have to add their CA/Issuer certificates myself. And I can add those certificates to all the Linux machines we have to maintain. Click to expand...
It's a royal mess. But you learn to live with it. In any case, by default security.enterprise_roots.enabled is set to false, in other words, it defaults to using it's own certificate store.
Karma: 3 Posts: 29
- Oct 8, 2023
- This site uses cookies to help personalise content, tailor your experience and to keep you logged in if you register. By continuing to use this site, you are consenting to our use of cookies. Accept Learn more…
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
- Contact Sales
- Try Azure for free
Public preview: Support for Key Vault Certificates in Azure Container Apps
Published date: march 27, 2024.
You can now use Azure Key Vault to store and manage your own TLS/SSL certificates for use with Azure Container Apps at the app and environment level. This follows security best practices by leveraging managed identities and simplifies management tasks like auto-rotation.
This feature is currently available in the Azure CLI and ARM, with some support for portal. Full portal support will be added over the next few months.
Learn more.
- Azure Container Apps
Related Products

Gypsy Rose Holds Hands with Ex-Fiancé Ken, Smoke Break at Dollar General

Guess The Sexy Legs Of This Actress!

Rashee Rice Admits To Driving Lamborghini In Dallas Car Crash

Travel With Chrissy Teigen And John Legend To Thailand For A Family Vacay!

Porch Thief Steals Package From Home Disguised As Trash, Caught on Video
Conjoined twin abby hensel's sister brittany not listed as wedding witness, conjoined twin abby hensel sister brittany not listed as witness ... at 2021 wedding to josh.
Conjoined twin Abby Hensel did not list her sister, Brittany , as one of her witnesses at her wedding ... something we've now confirmed through an official document.
TMZ has obtained Abby and Josh Bowling 's marriage certificate, and it provides some interesting information, including the fact that Brittany Hensel -- who partially shares a body with Abby -- is not on the witness list ... although another Hensel sibling is.
Abby put down her other sister, Morgan , as one of her witnesses ... and somebody named Cosmo Naut is listed as the other witness, presumably offered up from Josh's side.
BTW, we're not entirely sure if "Cosmo Naut" is a person or not -- it's obviously a play on the actual word cosmonaut (a Russian astronaut) ... and this could well be a pet.
In any case ... there are a few other deets from the cert, including the fact they got married at the Jerome Event Center in Delano, MN. It was there that Rev. Sid A. Veenstra officiated their nuptials ... which, as we reported, went down in 2021 -- November 13, to be exact.
Also of note ... Abby changed her surname in the marriage, going from Hensel to Bowling.
As we reported ... word of Abby and Josh's marriage raised a lot of eyebrows, and got people asking a lot of questions -- which drew the ire of the twins on social media.
They were clearly annoyed with all the renewed attention they'd been getting -- especially over something that was technically old news ... but which had been kept private 'til now.
We've tried contacting Abby and Josh for further comment ... so far, no word back.
- Share on Facebook
related articles

Conjoined Twin Abby Hensel's Husband is Decorated Army Vet, 3 Deployments

Conjoined Twins Abby & Brittany Hensel Fire Back at Haters Over Wedding
Old news is old news be first.
Chinese signatures on graduation certificates upset northern Virginia police chief
A northern Virginia town has been excluded from a countywide police training academy after the town’s chief complained about Chinese signatures on trainees’ graduation certificates
FAIRFAX, Va. -- A northern Virginia town has been excluded from a countywide police training academy after the town's chief complained about Chinese signatures on trainees' graduation certificates.
Herndon Police Chief Maggie DeBoard complained that the academy director, Maj. Wilson Lee, used Chinese characters to sign the certificates that graduates receive when they complete training at the Fairfax County Criminal Justice Academy.
In an email sent last month and obtained by The Associated Press, DeBoard told Lee, “I just found out that the academy graduation certificates were signed by you in some other language, not in English. This is unacceptable for my agency. I don't want our Herndon officers to receive these and I am requesting that they are issued certificates signed in English, the language that they are expected to use as an officer.”
On March 18, the county’s deputy executive for safety and security, Thomas Arnold, wrote to DeBoard informing her that the county was terminating Herndon's affiliation with the academy.
In a statement, Herndon Town Manager Bill Ashton said the town is reviewing the incident.
He defended DeBoard. “It is unfortunate that Chief DeBoard’s recent interaction with Fairfax County’s Criminal Justice Academy has been viewed as discriminatory. I have personally known Chief DeBoard for over 12 years and this interaction is completely inconsistent with the dedicated public servant that I know,” Ashton said.
The Town of Herndon is a part of Fairfax County, just outside the nation's capital, but the town maintains its own police force. The much larger Fairfax County Police Department is the primary user of the academy, which also serves the town of Vienna, the county sheriff's office and the county fire marshal.
Fairfax County Police Chief Kevin Davis declined to comment on the dispute. But in an email he sent to officers, he defended Lee, saying. “For 16 years of an impeccable career, memorializing a legal name given at birth with a signature that exudes heritage pride has not garnered a single criticism. Nor should it.”
Last year, a former Herndon police officer sued the town in federal court, saying she suffered sexual harassment and discrimination at the hands of a supervisor. The lawsuit accused DeBoard of failing to stop the harassment even though she was aware of it.
The lawsuit was eventually settled before trial, but court papers indicate that other officers complained of racial discrimination during the time DeBoard has been chief.
In the court papers, the town said DeBoard took the female officer's concerns seriously and that she would have recommended firing the officer accused of harassment, but he resigned before she could do so. Lawyers for the town said the complaints of racial discrimination were made by officers who faced disciplinary action.
Herndon Police referred questions Wednesday to the statement issued by the town manager.
Top Stories

Judge denies Trump's motion to have Georgia case dismissed on 1st Amendment grounds
- Apr 4, 2:09 PM

Why April's total solar eclipse will be a historic event in the US
- Apr 4, 10:23 AM

Elderly American tourist killed in elephant attack while on safari in Zambia
- Apr 4, 9:43 AM
Total solar eclipse forecast: Clouds could block eclipse in these areas
- Apr 4, 11:52 AM

New York AG questions whether California company can handle Trump's $175M bond
- 3 hours ago
ABC News Live
24/7 coverage of breaking news and live events
Keychain Access User Guide
- What is Keychain Access?
- View the information stored in a keychain
- Add a password to a keychain
- Store confidential information securely
- Copy keychains
- Create an identity preference
- Import and export keychain items
- Delete a keychain
- Get information about a certificate
- Determine if a certificate is valid
- Change the trust settings of a certificate
- Request a certificate from a certificate authority
- Add certificates to a keychain
- Create your own certificate authority
- Create self-signed certificates
- Issue new certificates
- Create a certificate preference
- Keyboard shortcuts
- If your Mac keeps asking for your keychain password
- If you’re asked for access to your keychain
- If a trusted app asks for keychain access
- If you need to update your keychain password
- If you forget an app or server password
- If you receive an invitation from a certificate authority

Get information about a certificate in Keychain Access on Mac
Use Keychain Access to view the information contained in a certificate .
Open Keychain Access for me

IMAGES
VIDEO
COMMENTS
Previous shared Trust Stores. Beginning with iOS 12, macOS 10.14, tvOS 12, and watchOS 5, all four Apple operating systems use a shared Trust Store. As the Trust Store version is updated, previous versions are archived here: List of available trusted root certificates in iOS 16.5, iPadOS 16.5, macOS 13.5, tvOS 16.5, and watchOS 9.5.
This seems to be because Safari and Chrome use the OS root certificate store and Firefox uses its own, and El Capitan is not being updated. From here there are: Trusted certificates establish a chain of trust that verifies other certificates signed by the trusted roots — for example, to establish a secure connection to a web server.
1. There is another freeware Inspect - View TLS certificate. - Franklin Yu. Nov 7, 2021 at 4:07. 1. TLS Inspector also adds a convenient feature to view the certificate straight from Safari: tap the Share button and scroll down to the Show Certificate option. - dregad.
Safari's client certificates and related preferences are stored in Keychain Manager with a kind of certificate. When you select a certificate to use with a web site, it stores another entry in the Keychain Manager with a kind of identity preference. Unfortunately, by default it stores it only for the exact page you were on.
Apple operating systems and applications (such as Safari and Mail) use a common store for root certificates; ... All CA Certificates subordinate to the applicant Root CA Certificate must ... Shop the Apple Online Store (1-800-MY-APPLE), visit an Apple Retail Store, or find a reseller. Apple Info; Site Map;
I think the problem lays in the shared Trust Store. There you can still find the expired certificate. And if a device used this once for a site, it tries to use it again. ... devices, and web server (TLS Server certificates). In both devices, Safari shown connection are not private. When tested the same in Windows and Android (Samsung Galaxy ...
Enter your Kerberos username, Kerberos password, and MIT ID number, and click Continue. Result: The Request Certificate screen is displayed. Enter a Certificate Life, or leave the default value (the maximum certificate life), and click Continue. Note: Most users should accept the default value. Result: The Install Your Certificates screen is ...
The first location is where my personal keychain is stored. To access their data, I need the Keychain Utility located in the Utilities folder in the Applications folder. I like using spotlight to access the Keychain Utility as it only takes a few keys to get there - click on the spotlight icon in the top right corner and type "keychain".
Step #1. Open the website in Chrome. Step #2. Click on the small padlock from the left of the URL. Step #3. Click on Certificate (Valid) from the small dropdown pop-up. Step #4. Here you have a summary of the certificate information. Click on Details to view the entire certificate.
3) Sign into your developer account at developer.apple.com, then click on Certificates, Identifiers & Profiles in the sidebar, and then click on Identifiers in the sidebar. 4) Click on the dropdown menu at the top right corner of the screen and select Website Push IDs. 5) Click on the website push ID to select it.
System Root Certificates. To better protect Apple customers from security issues related to the use of public key infrastructure certificates and enhance the experience for users, Apple products use a common store for root certificates. You may apply to have your root certificate included in Apple products via the Apple Root Certificate Program.
Resolution. Security Certificate Errors. DigiCert SSL certificates expiring after January 2011 are issued from a 2048 bit certificate path. The Root Certificate in this path is titled "DigiCert High Assurance EV Root CA" and is already trusted by all modern browsers (Internet Explorer, Firefox, Safari, Opera, Chrome, etc.)
Webを超高速で閲覧でき、強力なプライバシー保護機能と強力なカスタマイズオプションを備えています。. Safariでは、サイトをブラウズしたり、Webページを翻訳したり、開いているタブにiOS、iPadOS、macOSのすべてでアクセスしたりできます。. 機能. • iPhone ...
Safari West Presents! Zooarchaeologist Jun Sunseri Saturday April 6, 2024 | 8:00pm - 8:30pm. Conservation Dinner Series: Kojun "Jun" Ueno Sunseri, Ph.D., RPA joins us in the elephant room after dinner to give a talk about bones/skulls. Explore Share
And the desktop hosting team hasn't configured this. Which is funny, because I am allowed to add CA certificates to Firefox's store. So it's always a pain when they connect a new client and I have to add their CA/Issuer certificates myself. And I can add those certificates to all the Linux machines we have to maintain.
You can now use Azure Key Vault to store and manage your own TLS/SSL certificates for use with Azure Container Apps at the app and environment level. This follows security best practices by leveraging managed identities and simplifies management tasks like auto-rotation.
install SSL certificates on Firefox browsers separately if your organization allows Firefox browsers. Google Chrome, however, uses the same certificate store as Internet Explorer. • Certain client applications, like Dropbox, use a technique called Certificate Pinning, where the client application is hard coded to accept only one specific
TMZ has obtained Abby and Josh Bowling's marriage certificate, and it provides some interesting information, including the fact that Brittany Hensel -- who partially shares a body with Abby -- is ...
FAIRFAX, Va. -- A northern Virginia town has been excluded from a countywide police training academy after the town's chief complained about Chinese signatures on trainees' graduation certificates ...
In the Keychain Access app on Mac, select a keychain, then click either the My Certificates category or the Certificates category to see the certificates in that keychain. Select the certificate you want to view, then click the Info button in the toolbar. You can also double-click the certificate you want to view. Use Keychain Access on your ...