- Artsy Engineering Blog
- Our Open Source
- @artsyopensource
Hacking Around Safari's 7-day Cookie Limit
By christopher pappas.
Amongst the many, many things that organizations have to contend with around cookie consent laws is Apple’s very own browser, Safari. Did you know that Safari will only retain a client-side cookie for 7 days? This is in support of Apple’s Intelligent Tracking Prevention (ITP) feature, designed to protect a user’s privacy.
These privacy efforts are great but, in hand with laws like GDPR and CCPA , their rollout often creates a UX nightmare for users without some extra care. Here at Artsy, we’ve landed on a way to make things slightly less bad and want to share our approach.
Scenario: Imagine that as a EU resident you visit artsy.net for the first time. A banner appears asking you to Accept or Deny tracking cookies from our site. You don’t like tracking cookies, so you click the “Deny” button and the banner disappears. All good, right? Nope! You visit Artsy a week later and again, a banner appears asking you to choose your preferences. This happens again and again until you switch browsers and realize that what you were experiencing was Apple’s ITP feature in action. After choosing your preferences, the cookie we use to store them is erased after 7 days, necessitating another interaction.
We thrashed around in this vicious cycle for months until we found a simple, elegant solution thanks to a WebKit engineer’s prompt (during Apple’s open lab calls at WWDC – which you too can schedule! ) She mentioned that the 7-day cookie limitation only applies to client-side cookies and that same-domain, secure, server-side cookies are not limited to these constraints.
This got us thinking. Our third-party cookie consent management service sets a client-side cookie, not a server-side cookie. Could we perhaps overwrite the client-side cookie with a server-side cookie of the same name and trick Safari into persisting the user preferences beyond the 7-day limit?
We gave it a try and… Yes. We. Can! And this means that you can too (and it’s also real easy to implement).
First, define an API endpoint server-side:
Next, call the endpoint from the client when your app boots or when preferences have been set by the user:
And that’s it. I’m not sure of the exact reason why we can overwrite cookies in this way, but I suspect it has to do with Safari’s assumption that a server we control will always take precedence and thus assumes things are safe. And in 7 days, when Safari would otherwise erase the cookie, it will see that it’s now secure and ignore it, preserving the user’s preferences.

Safari's 7-Day Expiration for Authentication Cookies: An Overview
Abstract: This article discusses Safari's unusual behavior of limiting the expiration time of authentication cookies to 7 days. Understand the implications and potential workarounds.
Safari Limiting Auth Cookies to 7 Days: A Comprehensive Overview
In the world of Single Page Applications (SPAs) and web development, authentication is a critical aspect of ensuring a secure and seamless user experience. One of the key components of authentication is the use of cookies, which store user information and allow for easy access to protected resources. However, Apple's Safari browser has implemented a seven-day expiration limit on first-party cookies, which can be confusing and challenging for developers to work around.
Understanding First-Party Cookies
First-party cookies are those that are set by the same domain as the website that the user is currently visiting. For example, if a user visits mydomain.com , any cookies set by that domain would be considered first-party cookies. These cookies are essential for many website functionalities, including authentication, session management, and personalization.
Safari's 7-Day Expiration Limit
In an effort to improve user privacy, Safari has implemented a seven-day expiration limit on first-party cookies. This means that any first-party cookie set by a website will be automatically deleted after seven days, regardless of whether the user is still actively using the site. While this is a positive step for user privacy, it can create challenges for developers who rely on cookies for authentication and other functionalities.
Impact on SPA Hosted Apps
The seven-day expiration limit can be particularly challenging for Single Page Applications (SPAs) that are hosted on a separate domain from the API that serves the cookies. For example, if a SPA is hosted on app.mydomain.com , but the API that sets the authentication cookie is hosted on api.mydomain.com , the cookie will still be considered a first-party cookie by Safari and subject to the seven-day expiration limit.
Potential Workarounds
While there is no perfect workaround for Safari's seven-day expiration limit, there are a few strategies that developers can use to mitigate its impact:
Use local storage: Local storage is a web API that allows developers to store data on the user's device. Unlike cookies, local storage is not subject to the seven-day expiration limit in Safari. However, it is important to note that local storage is not sent with every HTTP request, so it may not be suitable for all use cases.
Prompt users to re-authenticate: Developers can prompt users to re-authenticate after seven days, ensuring that the authentication cookie is always fresh. While this can be a frustrating user experience, it is a reliable way to ensure that the user remains authenticated.
Use a longer expiration time: While Safari will still automatically delete the cookie after seven days, setting a longer expiration time can help to ensure that the user remains authenticated for as long as possible. However, this strategy should be used with caution, as it can create security risks if the user is inactive for an extended period of time.
Safari's seven-day expiration limit on first-party cookies can be a challenging hurdle for developers to overcome. However, by understanding the limitations and exploring potential workarounds, it is possible to create a secure and seamless user experience for Safari users.
Web Storage API: https://developer.mozilla.org/en-US/docs/Web/API/Web_Storage_API
Cookie Security: https://owasp.org/www-community/HttpOnly
Session Management Cheat Sheet: https://cheatsheetseries.owasp.org/cheatsheets/Session_Management_Cheat_Sheet.html
Learn more about Safari's 7-day cookie limit for authentication in software development.
Understanding parent component passing of router config properties in react router 6.
In this article, we will explore how to pass custom router config properties from a parent component to a child component using React Router 6.
Understanding the Use of CancellationToken in BulkExecuteUpdateAsync
In this article, we will explore the use of CancellationToken in BulkExecuteUpdateAsync, a method commonly used for performing multiple database updates in parallel.
Preventing Windows 11 from Sleeping: Essential Combinations
Learn the essential combinations to prevent Windows 11 from sleeping during software development projects. Keep your system awake with these simple methods.
Solving Matlab Error: 'Unrecognized field name rowheaders'
In this article, we will discuss how to solve the Matlab error 'Unrecognized field name rowheaders'. This error occurs when using Matlab with minimal coding experience, and the emission wavelengths are not recognized as valid field names. We will provide a solution to this issue.
Tags: : Safari Cookies Authentication
Latest news
- Building Shared DLLs in Windows: A Look at duckdb
- Custom Domain Causing Set-Cookie: Blocked Domain Attribute Invalid Regards Current Host URL
- Dynamically Select Rows in Another Sheet Based on Sheet Name and Query
- Troubleshooting PHP Executable Not Found Error in XAMPP
- Model.io Export of USDZ Files to STL Results in 'Client Not Entitled' Error
- Using Option Block, Input Capture, and Command in Terraform with Rundeck
- Detecting % Symbol in 3 of 9 Barcode Font: A Solution
- Registering a Variable with Multiple Conditions in Ansible
- Understanding Deallocation in NSTextView using Objective-C on MacOS
- Resolving Issues with YAML Kubernetes Deployment Files
- Debugging Closure Properties with Chrome DevTools: A Deep Dive into the 'Scope' Section
- Dismissing Sheet: Load New Viewsheet Dismissed in Game Development
- Implementing Sign-In with Google using FastHTML: A Comprehensive Guide
- Spring Boot: Native Image Build Failed
- Troubleshooting WebSocket Connection Failures with PHPRatchet
- Selecting Collections: Working with MatTable in Angular
- Weld Not Detecting @Inject Jetty 12 with Java 21 Apache Wicket
- Godot: Unable to Find Node for Texture Progress Bar in Enemy's Health
- Challenges with SignInWithPopup in Background.js for Chrome Extensions with Firebase
- Applying White Boundary Plotting Mask with Grey Overlay
- Retaining Previous Test Results While Running Azure Test Plans
- Modifying Values in DT filtering Sliders with RShiny and JavaScript
- Exploring RDMA: Allowing Remote Memory Mapping to Local Virtual Memory in OpenSHMEM UPC
- Internationalizing a FastAPI Websocket Server: Handling Multiple Clients and JSON Messages
- Restoring Access to Bookmarked URLs in SwiftUI with SQLite
- Error in Importing SQL Magics: escaping string literals with colon prefix
- Livewire's Long Rendering Select Field in Locations Table: Solutions
- Using AlpineJS with Django-Cotton Components: A Solution
- Proper Thread Closing: Preventing Infinite Loops in Python Background Tasks
- Troubleshooting vis.gam() Problem: Plotting Without Colors in Perspective View
- Fixing Broken Links and Missing Blobs in a Github Repository: Restore Normal Behavior
- Restricting User Access to Specific Content Based on IP Address using PHP
- Stripe.js Fails to Load in Android WebView React Native App
- Customizing the Appearance of Horizontal Bar Charts in MPAndroidChart (Kotlin) - Changing Gridlines and Axis Colors
- Working with Negative Sets in JavaScript Regex: An Unexpected Observation
Clear the history, cache, and cookies from Safari on your iPhone, iPad, or iPod touch
Learn how to delete your history, cookies, and cache in Settings.
Delete history, cache, and cookies
Clear cookies and cache, but keep your history, delete a website from your history, block cookies, use content blockers.
Go to Settings > Safari.
Tap Clear History and Website Data.
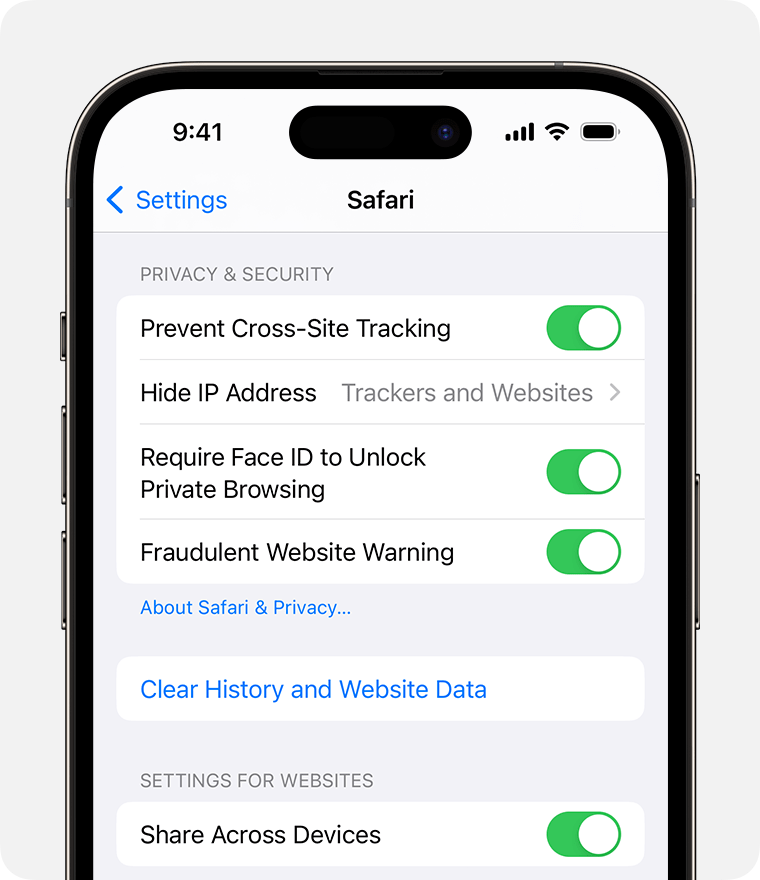
Clearing your history, cookies, and browsing data from Safari won't change your AutoFill information.
When there's no history or website data to clear, the button to clear it turns gray. The button might also be gray if you have web content restrictions set up under Content & Privacy Restrictions in Screen Time .
To visit sites without leaving a history, turn Private Browsing on .
Go to Settings > Safari > Advanced > Website Data.
Tap Remove All Website Data.
When there's no website data to clear, the button to clear it turns gray. The button might also be gray if you have web content restrictions set up under Content & Privacy Restrictions in Screen Time .
Open the Safari app.
Tap the Edit button, then select the website or websites that you want to delete from your history.
Tap the Delete button.
A cookie is a piece of data that a site puts on your device so that site can remember you when you visit again.
To block cookies:
Go to Settings > Safari > Advanced.
Turn on Block All Cookies.
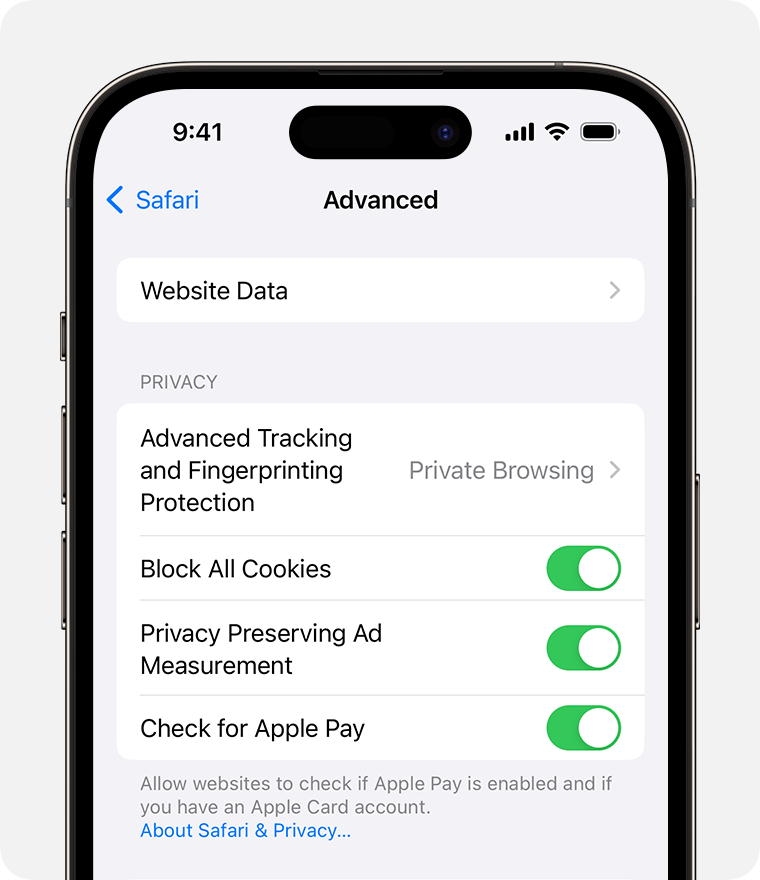
If you block cookies, some web pages might not work. Here are some examples:
You will likely not be able to sign in to a site even when using your correct username and password.
You might see a message that cookies are required or that your browser's cookies are off.
Some features on a site might not work.
Content blockers are third-party apps and extensions that let Safari block cookies, images, resources, pop-ups, and other content.
To get a content blocker:
Download a content blocking app from the App Store.
Tap Settings > Safari > Extensions.
Tap to turn on a listed content blocker.
You can use more than one content blocker. If you need help, contact the app developer .
Information about products not manufactured by Apple, or independent websites not controlled or tested by Apple, is provided without recommendation or endorsement. Apple assumes no responsibility with regard to the selection, performance, or use of third-party websites or products. Apple makes no representations regarding third-party website accuracy or reliability. Contact the vendor for additional information.

Related topics

Explore Apple Support Community
Find what’s been asked and answered by Apple customers.
Contact Apple Support
Need more help? Save time by starting your support request online and we'll connect you to an expert.
.png)
- 858-876-5323
Member Login
- Performance Marketers - Get Listed Today
- Search Companies
- Company Reviews
- Company by Category
- Advertise Your Company
- Industry Events
- Search Jobs
- Discussions
- Community Articles
Safari ITP Update: Implications for Advertisers with 7-Day Cookie Limit on Responses from Third-Party IPs

Apple's Safari browser recently updated its Intelligent Tracking Prevention (ITP) system, introducing a 7-day limit on cookies generated by third-party IP addresses. This enhancement to Safari's privacy features is aimed at improving user privacy by limiting the tracking capabilities of third-party entities. In this article, we will explore how this change might impact advertisers and their digital marketing strategies.
- Challenges in User Tracking and Data Collection
The ITP update primarily affects advertisers who depend on cookies to monitor user behavior, deliver personalized content, and track conversions. The new 7-day limitation on third-party cookies will restrict their ability to collect extensive user data and maintain long-term tracking of users' browsing habits. Consequently, advertisers may face challenges in understanding and analyzing consumer preferences and behavior, which could impact the efficiency of their ad targeting.
- Reduced Effectiveness of Retargeting Campaigns
Retargeting campaigns, which rely on tracking users who have previously visited a website or engaged with an ad, may become less effective due to the shortened cookie lifespan. Advertisers will have a smaller window to deliver targeted ads based on past user interactions, leading to potential decreases in ad relevance and conversion rates.
- Limited Attribution and Conversion Tracking
The 7-day cookie limit will also affect advertisers' ability to track conversions and attribute them to specific marketing channels or campaigns. With the reduced tracking capabilities, it may become more challenging to determine the effectiveness of different campaigns and allocate resources accordingly.
- Shift in Advertising Strategies
To adapt to the new cookie limitations, advertisers may need to shift their focus from third-party data collection to first-party data and other privacy-compliant tracking methods. This could involve investing more in content marketing, search engine optimization, and social media advertising, where user data can be collected directly from interactions with the brand.
- Emphasis on Alternative Tracking Methods
In response to the ITP update, advertisers should explore alternative tracking methods that respect user privacy. Some potential solutions include first-party data collection, server-side tracking, and consent-based tracking mechanisms. By adopting privacy-first approaches, advertisers can maintain compliance with evolving privacy regulations while continuing to provide personalized experiences to users.
- Collaboration with Publishers
Advertisers may need to foster stronger relationships with publishers to access first-party data and insights. By working closely with publishers, advertisers can develop strategies that leverage publisher-owned data to deliver more relevant and targeted ads.
In conclusion, the Safari ITP update that imposes a 7-day limit on third-party cookies from different IP addresses will significantly impact advertisers and their digital marketing strategies. Advertisers will need to adapt to the changing landscape by shifting their focus to first-party data, exploring alternative tracking methods, and collaborating more closely with publishers. By embracing these changes, advertisers can continue to deliver personalized ads while respecting user privacy.
Leave Comment Below
- Get Notified by Email for:
- Any New Comments
- Only Replies to My Comments
- Stop Following Comments
- Not a Registered User? Create Free User Account
- Are You a Local Business? List Your Company Now
Lead Generation World

Login to Send a Direct Message
Related posts.

- Finding Performance Marketers is easy by searching our trusted network of top-rated Performance Marketers.
- How It Works
- List Your Company
- Browse Categories
- Browse Locations
- Performance Marketing Directory
- All Rights Reserved
- Terms of Use
- Privacy Policy
Intelligent Tracking Prevention 2.3
Sep 23, 2019
by John Wilander
@johnwilander
Intelligent Tracking Prevention (ITP) version 2.3 is included in Safari on iOS 13, the iPadOS beta, and Safari 13 on macOS for Catalina, Mojave, and High Sierra.
Enhanced Prevention of Tracking Via Link Decoration
Our previous release, ITP 2.2 , focused specifically on the abuse of so-called link decoration for the purposes of cross-site tracking. With ITP 2.2, when a webpage is navigated to from a domain classified by ITP and the landing URL has a query string or fragment, the expiry of persistent client-side cookies created on that page is 24 hours.
Unfortunately, we see continued abuse of link decoration, so ITP 2.3 takes two new steps to combat this.
Capped Lifetime For All Script-Writeable Website Data
Since ITP 2.2, several trackers have announced their move from first-party cookies to alternate first-party storage such as LocalStorage. ITP 2.3 counteracts this in the following way:
- website.example will be marked for non-cookie website data deletion if the user is navigated from a domain classified with cross-site tracking capabilities to a final URL with a query string and/or a fragment identifier, such as website.example?clickID=0123456789 .
- After seven days of Safari use without the user interacting with a webpage on website.example, all of website.example’s non-cookie website data is deleted.
Together with ITP’s capped expiry of client-side cookies, this change removes trackers’ ability to use link decoration combined with long-term first-party website data storage to track users. Put differently, ITP 2.3 caps the lifetime of all script-writeable website data after a navigation with link decoration from a classified domain.
The reason why we cap the lifetime of script-writable storage is simple. Site owners have been convinced to deploy third-party scripts on their websites for years. Now those scripts are being repurposed to circumvent browsers’ protections against third-party tracking. By limiting the ability to use any script-writeable storage for cross-site tracking purposes, ITP 2.3 makes sure that third-party scripts cannot leverage the storage powers they have gained over all these websites.
document.referrer Downgraded To eTLD+1
Our research has found that trackers, instead of decorating the link of the destination page, decorate their own referrer URL and read the tracking ID through document.referrer on the destination page.
ITP 2.3 counteracts this by downgrading document.referrer to the referrer’s eTLD+1 if the referrer has link decoration and the user was navigated from a classified domain. Say the user is navigated from social.example to website.example and the referrer is https://sub.social.example/some/path/?clickID=0123456789 . When social.example’s script on website.example reads document.referrer to retrieve and store the click ID, ITP will make sure only https://social.example is returned.
For further reading on misuse of the referrer and changes coming to browsers in general, see the WHATWG Fetch issue Limit the length of the Referer header .
Updates To the Storage Access API
Developer enhancement requests.
Developers have asked us for two changes to the Storage Access API, and we’re happy to provide them in Safari on iOS 13 beta, iPadOS beta, and macOS Catalina beta:
- Only consume the user gesture (tap or click) when the user explicitly denies access , i.e. when the user is prompted and picks “Don’t allow.” Previously the gesture was also consumed when the promise was rejected without a user prompt, i.e. when the requesting domain was classified by ITP and had not received user interaction as first-party website the last 30 days of Safari use. This meant the user had to tap or click again to be shown a popup to log in to the third-party service.
- Make document.hasStorageAccess() return true when ITP is off . Developers were confused when document.hasStorageAccess() returned false but ITP was off. Now it returns true in that case. Note that a returned true does not guarantee that the third-party can set cookies since Safari’s default cookie policy is to deny cookies for third-parties if they don’t already have cookies.
User Enhancement Request
Users have asked us to cap the number of times they can get asked for storage access by a specific piece of embedded web content.
Some services are requesting storage access on every click or tap, regardless of previous interactions with the user. To counter such repeated prompting, WebKit’s implementation of the Storage Access API will now automatically reject the request for storage access for documents where the user has picked “Don’t Allow” in the prompt twice. The reason why we don’t cap it to a single prompt is that the user may change their mind when they see the result of picking “Don’t Allow” the first time.
We will restrict the API further if we get reports of continued over prompting.
ITP Debug Mode In Safari on macOS Catalina
Safari 13 on macOS includes ITP Debug Mode. It’s been available in Safari Technology Preview for quite some time but now it’s available in regular Safari too so that you can debug your websites with the same Safari your customers are using.
Below is a step-by-step guide on how to use ITP Debug Mode. Note that both menu placement and naming has changed from the earlier experimental feature.
If you prefer to use Console:
- Launch the Console app.
- Click the Action menu → Include Info Messages.
- Filter on “ITPDebug” without the quotes.
If you prefer to use Terminal:
Now you’re ready to enable ITP Debug Mode and see log output.
- Enable the Develop menu through Safari Preferences → Advanced → “Show Develop menu in menu bar.”
- Click “Intelligent Tracking Prevention Debug Mode” in the Develop menu.
- When you’re done, disable ITP Debug Mode through the same Develop menu item or by quitting Safari. Don’t leave ITP Debug Mode on when you’re not using it since it logs potentially sensitive information about your browsing. (Logging is done on the ephemeral INFO level.)
With ITP Debug Mode enabled, you will see ITP messages in the log as you browse the web. Whenever ITP decides to schedule deletion of website data it will indicate in the log “all data” or “all but cookies” to tell you whether it’s a regular deletion of all website data or the new capped lifetime of all non-cookie website data as explained above.
The domain 3rdpartytestwebkit.org is permanently classified with tracking capabilities in ITP Debug Mode, so at minimum you should see that domain show up in your log.
Classifying A Custom Domain For Testing
With ITP Debug Mode and User Defaults, you can manually set a custom domain as permanently classified with tracking capabilities. Here’s how you achieve this for a domain called website.example:
- Open System Preferences, click Security & Privacy, and unlock the padlock to be able to make changes.
- Pick the Full Disk Access category to the left.
- Use the + button to add the Terminal application to the list and make sure its checkbox is ticked.
- Open Terminal and execute the following command: defaults write com.apple.Safari ITPManualPrevalentResource website.example
- Go back to Security & Privacy in System Preferences and untick the checkbox for Terminal to not allow it permanent full disk access.
A Note On HttpOnly Cookies
Our blog post on ITP 2.1 provided guidance on how to protect cookies. We specifically encourage the use of Secure and HttpOnly cookies .
Since publishing that post, we’ve seen some confusion regarding the term HttpOnly cookie, sometimes mistakingly shortened to just “HTTP cookie.” Some say any cookie set by a server is an HttpOnly cookie. That is incorrect. The server needs to add the HttpOnly attribute in the Set-Cookie response header to make a cookie be HttpOnly, like so:
Adding the HttpOnly attribute provides these two security and privacy protections:
- HttpOnly cookies are not exposed to JavaScript. This means tracking scripts or cross-site scripting attacks on the website cannot read and leak the contents of those cookies.
- HttpOnly cookies are not copied into the web content process in WebKit. This means they are out of reach for speculative execution attacks that could otherwise steal the contents of those cookies.

IMAGES
VIDEO
COMMENTS
Hacking Around Safari's 7-day Cookie Limit By Christopher Pappas Aug 23, 2022. Amongst the many, many things that organizations have to contend with around cookie consent laws is Apple's very own browser, Safari. ... She mentioned that the 7-day cookie limitation only applies to client-side cookies and that same-domain, secure, server-side ...
This default cookie policy has been in effect since Safari 1.0 and is still in effect today as part of the "Prevent cross-site tracking" setting. ... The first-party domain of home screen web applications is exempt from ITP's 7-day cap on all script-writeable storage, i.e. ITP always skips that domain in its website data removal algorithm
Safari's 7-Day Expiration Limit. In an effort to improve user privacy, Safari has implemented a seven-day expiration limit on first-party cookies. This means that any first-party cookie set by a website will be automatically deleted after seven days, regardless of whether the user is still actively using the site.
It means once a request is blocked from using cookies, all redirects of that request are also blocked from using cookies. Back in 2017 we got a request to allow cookie blocking to open and close on redirects and implemented that behavior. But with full third-party cookie blocking in place, latch mode is back. 7-Day Cap on All Script-Writeable ...
Safari's new ITP restrictions (16.4) - April 2023. This is Simo Ahava's recent Linkedin post on the topic: Now, as of Safari 16.4 released in April 2023, Safari sets the lifetime of server-set first-party cookies to a maximum of 7 days in the following cases: The server setting the cookie is behind a CNAME that resolves (at any point) to ...
First-party cookies created by JavaScript's document.cookie will expire in 7 days. If the cookies are accessed within those 7 days, then their expiration date will be extended by 7 days. First-party cookies created by JavaScript's document.cookie AND are created by a tracking domain AND use link decoration will expire in 24 hours.
Here is a short timeline of the critical ITP updates: ITP limits third-party cookies by default to 7 days. ITP limits third-party cookies' lifetime to 24 hours if the URL has query parameters (like utm_source, click ids, etc.). ITP limits first-party cookies' lifetime to 7 days if they were set using CNAME cloaking.
Client-Side Cookies Capped to 7 Days of Storage. Cookies can either be set in HTTP responses or through the document.cookie API, the latter sometimes referred to as client-side cookies. With ITP 2.1, all persistent client-side cookies, i.e. persistent cookies created through document.cookie, are capped to a seven day expiry.
Block cookies. A cookie is a piece of data that a site puts on your device so that site can remember you when you visit again. To block cookies: Go to Settings > Safari > Advanced. Turn on Block All Cookies. If you block cookies, some web pages might not work. Here are some examples:
The Safari policy regarding cookies is not a strict seven-day time limit. It involves a counter for up to seven unused days. That means every time a user opens Safari and visits your website, your ...
Safari 13.1: Third-Party Cookie Blocking and 7-Day Script-Writeable Storage. John Wilander : Cookies for cross-site resources are now blocked by default across the board. This is a significant improvement for privacy since it removes any sense of exceptions or "a little bit of cross-site tracking is allowed." […]
Cookie 7-Day Cap on All Script-Writeable Storage … Now ITP has aligned the remaining script-writable storage forms with the existing client-side cookie restriction, deleting all of a website's script-writable storage after seven days of Safari use without user interaction on the site. In a nutshell, this means:
Apple's Safari browser recently updated its Intelligent Tracking Prevention (ITP) system, introducing a 7-day limit on cookies generated by third-party IP addresses. This enhancement to Safari's privacy features is aimed at improving user privacy by limiting the tracking capabilities of third-party entities.
This keeps the cookie alive in the users Safari browser for another 7 days and can continue to keep this alive upon the visitors return within 7 days. For example: You set consent expiry to 12 months in the manager. A user submits consent on May 3rd 2021 - the cookies' natural expiry will be set to May 3rd 2022.
Safari is limiting my auth cookie to 7 days. This is weird since: Should be a first party cookie (Cookie has Domain=.mydomain.com, my SPA hosted on app.mydomain.com and the API that serves the cookie on api.mydomain.com). It's not ITP related as far as I can see as I enabled "ITP debug mode" and didn't see my domain on the list of domains with cross-site tracking restrictions.
South Africa Safari: Embark on a 7-day safari adventure through the beautiful Sabi Sand famous for the big 5 and the big cats before ending the journey in ultra-luxury in. Menu. Safaris & Tours. Botswana (587) ... Cookie Settings; Blog; African Safari Costs; Contact Us; Change Currency USD $ Our Statistics. 18 safari countries; 204 parks and ...
Tanzania Safari: Indulge in a luxurious 7-day fly and drive safari experience that combines the convenience of air travel with the thrill of exploration on the ground. ... Cookie Settings; Blog; African Safari Costs; Contact Us; Change Currency USD $ Our Statistics. 18 safari countries; 204 parks and reserves; 11,802 tour packages;
The 7-day Tremisana Lodge Kruger Park Safari includes two4hr sunset drives on Balule Big 5 Reserve, two Bush BBQ, 4hr bush walk with armed ranger, 2 full days in Kruger on open gameviewer, 4hr sundowner drive, visit to Moholoholo Rehabilitation Centre, 3 hr game drive on Balule Big 5 Reserve, 4hr morning game drive, sunrise drive and Scenic highlights of Blyde River Canyon including a stop at ...
Intelligent Tracking Prevention (ITP) version 2.3 is included in Safari on iOS 13, the iPadOS beta, and Safari 13 on macOS for Catalina, Mojave, and High Sierra. Enhanced Prevention of Tracking Via Link Decoration. , focused specifically on the abuse of so-called link decoration for the purposes of cross-site tracking.
Experience the awe-inspiring spectacle of the Great Migration on this 7-day tour, focusing on the dramatic Mara River crossing. Witness thousands of wildebeest and zebras braving the river's currents, facing predators, and continuing their epic journey. This tour offers a perfect blend of wildlife adventure and cultural experiences.
With the Explorer tour Cape Town & Karongwe Private Safaris - Fly-In 7 Days, you have a 7 days tour package taking you through Cape Town, South Africa and 11 other destinations in South Africa. Cape Town & Karongwe Private Safaris - Fly-In 7 Days includes accommodation in a hotel as well as flights, an expert guide, meals, transport and more.
This tour takes you to Kenya's major parks! It is value for money, and you have a high chance of spotting the Big Five and the ugly five. The safari primarily focuses on wildlife observation, natural habitats, diverse ecosystems, cultural experiences, photography opportunities, and game drives led by knowledgeable guides that ensure adventure as you explore the parks.
On this special tour, we focus on bringing you heartwarming memories for your special moment. The tour starts and ends in Nairobi but in between you get to visit Ol Pejeta Conservancy which is well known as the world's largest black rhino sanctuary and home to two remaining northern white rhinos in the world, Lake Nakuru which habitats millions thousands of flamingoes and bird life and finally ...